Author: Cybernoz
Boston, USA, September 16th, 2024, CyberNewsWire Analysis of millions of real-world NHI secrets by Entro Security Labs reveals widespread, significant…
Boston, USA, September 16th, 2024, CyberNewsWire Analysis of millions of real-world NHI secrets by Entro Security Labs reveals widespread, significant…
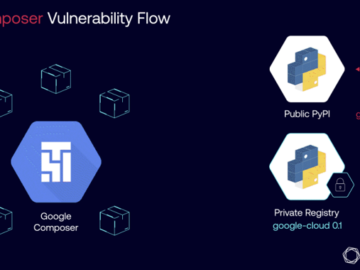
Sep 16, 2024Ravie LakshmananCloud Security / Vulnerability A now-patched critical security flaw impacting Google Cloud Platform (GCP) Composer could have…
HM Revenue & Customs’ (HMRC) publicly accessible list of non-compliant umbrella companies now features details of nearly 100 firms operating…
23andMe has reached a $30 million settlement to resolve a lawsuit related to a data breach that exposed the personal…
With the global cost of cybercrime reaching nearly $9.4 million in 2024, organizations are under immense pressure to protect their…
Medusa, a relatively new ransomware group, has gained notoriety for its dual-pronged online presence. Unlike its peers, Medusa maintains a…
Sep 16, 2024The Hacker NewsIdentity Protection / Incident Response Imagine this… You arrive at work to a chaotic scene. Systems…
SolarWinds fixed critical RCE CVE-2024-28991 in Access Rights Manager Pierluigi Paganini September 16, 2024 SolarWinds addressed a critical remote code…
A vulnerability in Azure API Management (APIM) has been identified. It allows attackers to escalate privileges and access sensitive information….
The Port of Seattle has officially confirmed that a cyberattack that disrupted its operations at the Seattle-Tacoma International Airport (SEA)…
A newly discovered vulnerability in the Spring Framework has been identified, potentially allowing attackers to access any file on the…