Author: Cybernoz
In a significant move that is set to reshape the cybersecurity landscape, Sophos has announced its acquisition of SecureWorks for…
Zero-Trust Endpoint Security: How a Preventive Approach Can Limit Your Endpoint Attack Surface Endpoint security has become more critical than…
We’ve got a hard truth to share with you, and you might not like it: You are not your software…
Those who hacked the Internet Archive haven’t gone away. Users of the Internet Archive who have submitted helpdesk tickets are…
Sophos has announced plans to acquire Secureworks for $859 million in a bid to improve its position in the XDR market…
Microsoft is warning of Windows crashing with the blue screen of death on some ASUS laptop models when trying to upgrade to…
Ransomware groups are cybercriminal organizations that deploy malware to encrypt victims’ data, which helps render it inaccessible until a “ransom”…
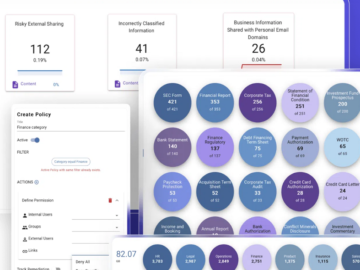
Data security is more critical than ever as organizations manage vast amounts of sensitive information across cloud and on-premises environments….
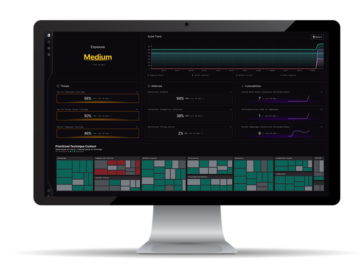
In the current cybersecurity landscape, the focus has shifted from merely managing vulnerabilities to strategically orchestrating defenses against targeted threats….
A hacker known as “TAINTU” is advertising a “Top Secret U.S. Space Force Military Technology Archive” for sale, allegedly containing…
In a significant development within the cybersecurity sector, two major players, Sophos and Secureworks, are poised to enter into a…
This week on the Lock and Code podcast… On the internet, you can be shown an online ad because of…