Author: Cybernoz
More than 70 percent of enterprises have prioritized SaaS security by establishing dedicated teams to secure SaaS applications, a trend…
The CTO Club recently picked the top 20 cybersecurity podcasts to enhance your ninja skills in 2024. Cybersecurity Ventures is the only…
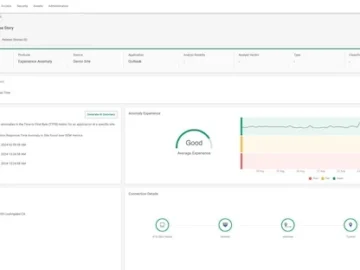
Cato Networks expanded the Cato SASE Cloud Platform by introducing Cato Digital Experience Monitoring (DEM). This announcement is the third…
As the United States enters full swing into its next presidential election, people are feeling worried, unsafe, and afraid. And…
A team of researchers from China has broken RSA encryption using quantum computing technology. Utilizing D-Wave’s advanced quantum annealing systems,…
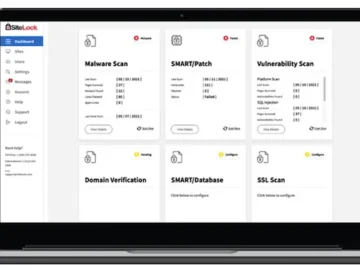
Sectigo announced SiteLock 2.0, a major upgrade to SiteLock, its website security and protection platform. SiteLock 2.0 is designed to…
In recent years, the number and sophistication of zero-day vulnerabilities have surged, posing a critical threat to organizations of all…
Last week, CISA added CVE-2024-23113 – a critical vulnerability that allows unauthenticated remote code/command execution on unpatched Fortinet FortiGate firewalls…
To tie in with the government’s International Investment Summit, US tech firms CyrusOne, ServiceNow, Cloud HQ, CoreWeave and ServiceNow have…
The European Union has officially adopted the Cyber Resilience Act, a new law that establishes stringent cybersecurity requirements for products…
In 2017, then 9-year-old Kayla Unbehaun was abducted. For years, the South Elgin, Illinois police department searched for Unbehaun and…
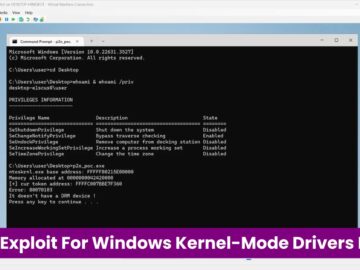
A critical vulnerability in Windows Kernel-Mode Drivers has been exposed with the release of a Proof-of-Concept (PoC) exploit, allowing attackers…