Author: Cybernoz
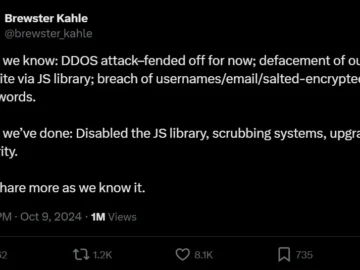
October 10, 2024 – The Internet Archive has been hit hard by a data breach and several DDoS attacks all…
A new and unconventional method of hacking has emerged. David Buchanan, a well-known hardware hacker, has demonstrated how a simple…
In today’s digital landscape, mobile devices have become integral to both personal and professional life. However, their widespread use also…
18 individuals and entities have been charged with widespread fraud and manipulation within the cryptocurrency markets. The charges, unsealed in…
We present a list of selected cybersecurity companies that received funding during the third quarter of 2024 (Q3 2024). Apono…
Amazon Web Services (AWS) is expanding its efforts to reuse and recycle its datacentre hardware by opening a reverse logistics…
The Internet Archive has faced a serious cybersecurity crisis that has taken both its Archive.org and OpenLibrary.org platforms offline. The…
If someone told you five years ago that you could pose questions to an AI agent about the most vexing…
A critical vulnerability has been identified in GitHub Enterprise Server, posing significant security risks by allowing attackers to bypass authentication…
While AI has captured the attention of the technology industry, the majority of CIOs and senior IT leaders are primarily…
Dubai, UAE – October 11, 2024 –GISEC Global, the largest and most influential cybersecurity event in the Middle East and…
In this Help Net Security interview, Rickard Carlsson, CEO at Detectify, discusses the evolution of attack surface management in the…