Author: Cybernoz
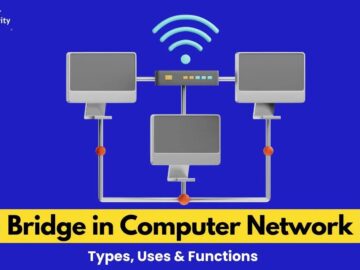
Various devices work together in computer networks to ensure seamless communication between network segments. The bridge plays a crucial role…
Discussions of insider risk inevitably conjure images of disgruntled IT employees stealing sensitive data from the comfort of an air-conditioned…
Austin, TX, USA, October 10th, 2024, CyberNewsWire IDLink, SpyCloud’s new automated digital identity correlation capability, is now core to its…
Austin, TX, USA, October 10th, 2024, CyberNewsWire IDLink, SpyCloud’s new automated digital identity correlation capability, is now core to its…
Calling future journalists! Episode 2 of the National Cryptologic Foundation’s #CyberChats Podcast features Steve Morgan, Founder of Cybersecurity Ventures, Editor-in-Chief at Cybercrime…
Mozilla has pushed out an emergency update for its Firefox and Firefox ESR browsers to fix a vulnerability (CVE-2024-9680) that…
A non-profit that benefits millions of people has fallen victim to a data breach and a DDoS attack. Internet Archive,…
Oct 10, 2024Ravie LakshmananVulnerability / Enterprise Security Cybersecurity security researchers are warning about an unpatched vulnerability in Nice Linear eMerge…
Internet search giant Google has hit back at the US Department of Justice’s (DoJ) suggestion that its operations should be…
The U.S. Securities and Exchange Commission (SEC) has announced fraud charges against three companies and nine individuals involved in crypto…
Wireshark, the world’s leading network protocol analyzer, has just released version 4.4.1, bringing a host of bug fixes and updates…
The current SOC model relies on a scarce resource: human analysts. These professionals are expensive, in high demand, and increasingly…