Author: Cybernoz
A data breach at Financial Business and Consumer Solutions (FBCS), a US debt collection agency, has led to the loss…
Universal Music data breach impacted 680 individuals Pierluigi Paganini October 07, 2024 Universal Music Group notified hundreds of individuals about…
Qualcomm has released security patches for a zero-day vulnerability in the Digital Signal Processor (DSP) service that impacts dozens of…
Google has announced the launch of an enhanced fraud protection pilot for Android users in the country. This initiative aims…
After what seemed like a long hiatus, we’ve observed threat actors returning to malvertising to drop malware disguised as software…
American Water, the largest publicly traded U.S. water and wastewater utility company, was forced to shut down some of its…
PowerShell-based malware is a form of fileless malware that exploits PowerShell to execute malicious scripts directly in memory which helps…
Net-zero by 2050 seems further away than ever. Google and Microsoft admitted their emissions are rising from artificial intelligence (AI)-related datacentre…
OATH Toolkit is a software suite that is primarily designed to implement OTP authentication systems. It includes libraries and command-line…
Nick Read has overseen a collapse in trust of the Post Office and not only as a result of the…
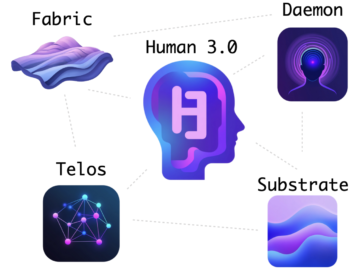
When people look at the various projects I’ve put out over the last year, they often ask which is the…
Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has partnered with Hybrid Analysis, a…