Author: Cybernoz
Two Chinese nationals were sentenced to prison for scamming Apple out of more than $2.5 million after exchanging over 6,000…
Threat actors are increasingly relying on Telegram and Discord apps for data exfiltration. Analysts at ANY.RUN shared a detailed guide…
At DEF CON 32, the SquareX research team delivered a hard-hitting presentation titled Sneaky Extensions: The MV3 Escape Artists where…
San Francisco, United States / California, October 3rd, 2024, CyberNewsWire Doppler, the leading platform in secrets management, today announces the…
For years, securing a company’s systems was synonymous with securing its “perimeter.” There was what was safe “inside” and the…
The United States District Court for the District of Columbia has today (3 October) unsealed a civil action brought by…
If your organization is like many, your employees may be relying on weak or easily guessable passwords — and inadvertently…
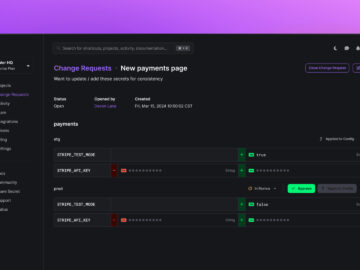
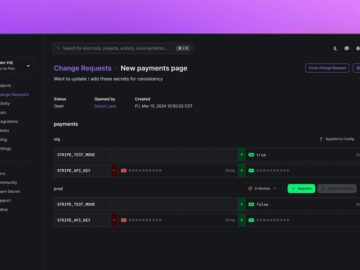
Doppler, the leading platform in secrets management, today announces the launch of Change Requests, a new feature providing engineering teams…
Doppler, the leading platform in secrets management, today announces the launch of Change Requests, a new feature providing engineering teams…
San Francisco, United States / California, October 3rd, 2024, CyberNewsWire Doppler, the leading platform in secrets management, today announces the…
Europol, in collaboration with various global law enforcement agencies, has broadened its Operation Cronos to apprehend four individuals allegedly connected…
CVE-2024-29824, an unauthenticated SQL Injection vulnerability in Ivanti Endpoint Manager (EPM) appliances, is being exploited by attackers, the Cybersecurity and…