Author: Cybernoz
International law enforcement has worked for years to disrupt the cybercriminal gang Evil Corp and its egregious global crime spree….
Did you know that over 80% of web applications fail due to poor planning and execution? Now imagine a framework…
The threat actors behind the Rhadamanthys information stealer have added new advanced features to the malware, including using artificial intelligence…
What Is Broken Access Control? BAC is a class of application vulnerability where a function or asset in the application…
The Evil Corp cybercrime syndicate has been hit with new sanctions by the United States, United Kingdom, and Australia, with…
XWorm refers to a type of malware that has been analyzed for its obfuscation techniques and potential impacts on systems….
Checkmarx researchers discovered PyPI malware posing as crypto wallet tools. These malicious packages stole private keys and recovery phrases, targeting…
The Evil Corp Cyber Attack on NATO Countries The notorious Russian state-funded cyber threat group known as Evil Corp has…
Iran-linked threat actors have become increasingly active in 2024, but one such group has so far gone relatively unnoticed. Handala…
Law enforcement authorities from 12 countries arrested four suspects linked to the LockBit ransomware gang, including a developer, a bulletproof…
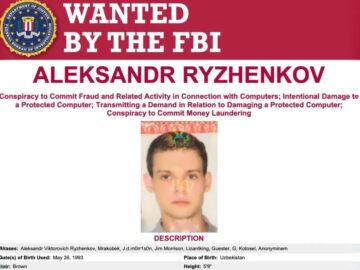
Law enforcement agencies have identified Russian national Aleksandr Viktorovich Ryzhenkov as a key member of the notorious Evil Corp cybercrime…
The UK’s National Crime Agency (NCA) has named and shamed a high-profile LockBit affiliate as its ongoing Operation Cronos takedown…