Author: Cybernoz
A critical vulnerability in NVIDIA Container Toolkit impacts all AI applications in a cloud or on-premise environment that rely on it…
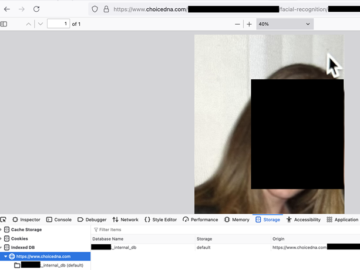
ChiceDNA exposed 8,000 sensitive records, including biometric images, personal details, and facial DNA data in an unsecured WordPress folder. Privacy…
Critical security vulnerabilities have been disclosed in six different Automatic Tank Gauge (ATG) systems from five manufacturers that could expose…
Yet, the road to successful AI integration is fraught with challenges, evidenced by numerous companies stepping back from their pilot…
Microsoft warns that some Windows 11 systems enter reboot loops or might freeze with blue screens after installing the September…
Recent investigations by cybersecurity experts have uncovered valuable insights into detecting human-operated ransomware attacks through Windows Event Logs. This breakthrough…
Simon Kaura, a Nigerian national deported from the United Kingdom, was sentenced in a U.S. federal court for his involvement…
The French news agency Agence France-Presse (AFP) has announced that it has been targeted by a cyber intrusion. The AFP…
Bishop Fox has introduced Broken Hill, an advanced automated tool created to produce tailored prompts that can circumvent restrictions in…
Microsoft has made changes to Recall – the screenshot-taking, AI-powered search feature for Copilot+ PCs running Windows 11 – to…
Imagine a sophisticated cyberattack cripples your organization’s most critical productivity and collaboration tool — the platform you rely on for…
A British national has been charged for his execution of a hack-to-trade scheme Pierluigi Paganini September 30, 2024 The Department…