Author: Cybernoz
CISO Guardz | Israel | Hybrid – View job details As a CISO, you will develop and implement security policies…
35% of employees lack confidence that they have the skills required to succeed in their roles, according to Skillsoft. Additionally,…
Compromised identities have been a central component of countless costly breaches this year, according to Red Canary. Rise in identity…
Cybercriminals are exploiting the ongoing Sean “Diddy” Combs scandal by spreading the new PDiddySploit malware hidden in infected files, targeting…
In many ways, the Cyber Security and Resilience Bill announced in the King’s Speech is long overdue. The Bill is described as an “urgent update…
Image: MidjourneyMicrosoft has released the September 2024 non-security preview update for Windows 10, version 22H2, with fixes for bugs causing…
AutoCanada is warning that employee data may have been exposed in an August cyberattack claimed by the Hunters International ransomware…
Victoria’s Department of Families, Fairness and Housing (DFFH) has been directed to ban and block access to a range of…
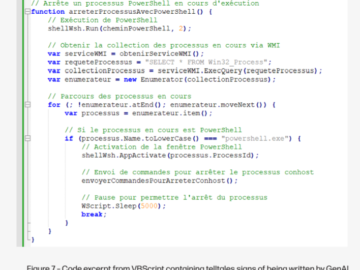
A generative artificial intelligence malware used in phishing attacks Pierluigi Paganini September 24, 2024 HP researchers detected a dropper that…
The US Department of Justice has sued Visa for alleged antitrust violations, accusing one of the world’s largest payment networks…
Image: MidjourneyArkansas City, a small city in Cowley County, Kansas, was forced to switch its water treatment facility to manual…
Vulnerabilities in Versa Director are never a small matter, as the platform manages network configurations for Versa’s SD-WAN software –…