Author: Cybernoz
Flax Typhoon is a cyber threat actor observed using legitimate software to gain unauthorized access to organizations in Taiwan. This…
In today’s fast-evolving digital landscape, cyber attackers are becoming increasingly creative, targeting the human element as a primary entry point….
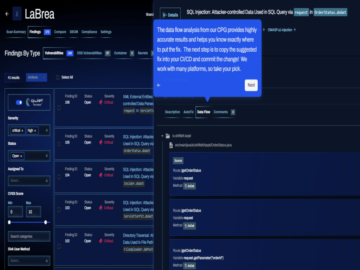
The volume of code needed is greater than ever while cycles to produce said code are shrinking. One of the…
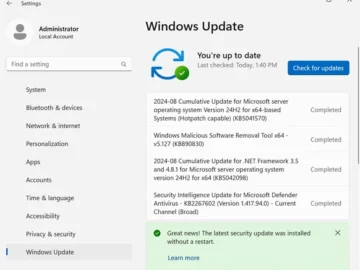
Organizations that plan to upgrade to Windows Server 2025 once it becomes generally available will be able to implement some…
Artificial intelligence (AI) continues to evolve at an unprecedented pace, with AI agents emerging as a particularly powerful and transformative…
Shells serve as user interfaces that allow interaction with an operating system’s services. They enable users to execute commands, run…
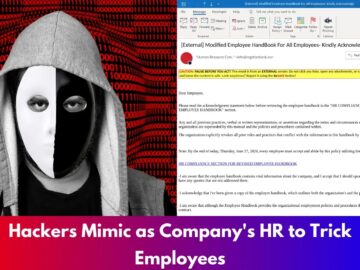
Hackers are now impersonating company Human Resources (HR) departments to deceive employees into revealing sensitive information. This latest phishing tactic…
In April 2023, the Cybersecurity and Infrastructure Security Agency (CISA) unveiled the Secure by Design initiative, setting a new standard for…
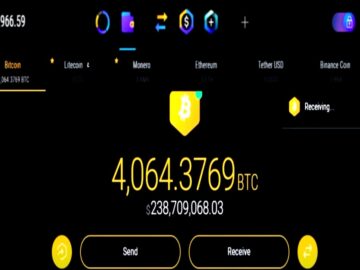
Hackers stole $243M from a single victim by posing as Google and Gemini support, resetting 2FA to access crypto. Investigator…
23 Sep U.S. Department Of Energy CISO: We Give Ourselves Poor Marks In Cybersecurity Posted at 08:43h in Blogs by…
A cybercriminal has released internal data online that they say has come from leaks at several high-profile sources, including SpaceX,…
Quantum computing revolutionizes various fields, leveraging the unique properties of quantum mechanics. Its impact on cybersecurity, however, presents both significant…