Author: Cybernoz
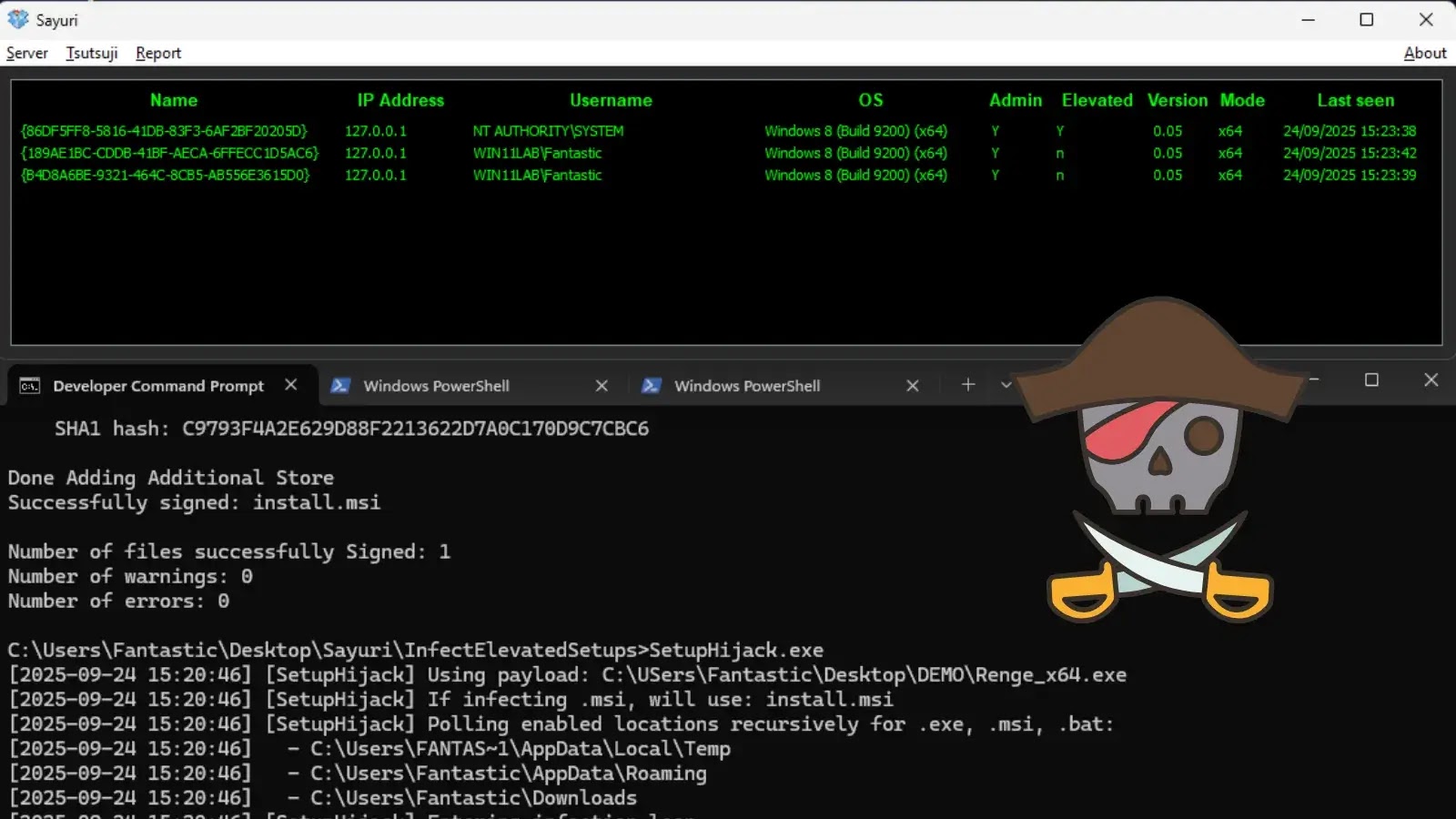
Security researchers at Hacker House have released SetupHijack, a proof-of-concept tool that exploits race conditions and insecure file handling in…
ESET Research has published new findings on DeceptiveDevelopment, also called Contagious Interview. This North Korea-aligned group has become more active…
Sep 25, 2025Ravie LakshmananSoftware Security / Malware Cybersecurity researchers have discovered two malicious Rust crates impersonating a legitimate library called…
Zoom has thrown down the gauntlet in the enterprise artificial intelligence (AI) race, with the announcement that AI Companion 3.0…
Cisco on Wednesday announced patches for 14 vulnerabilities in IOS and IOS XE, including a bug that has been exploited…
Numerous mobile applications have been found to expose critical user information through misconfigured Firebase services, allowing unauthenticated attackers to access…
Threat actors from the Lone None group are exploiting copyright takedown notices to distribute sophisticated malware, including Pure Logs Stealer…
Sensitive data is everywhere and growing fast. A new report from Concentric AI highlights how unstructured data, duplicate files, and…
Cisco fixed actively exploited zero-day in Cisco IOS and IOS XE software Pierluigi Paganini September 25, 2025 Cisco addressed a…
Organizations commonly allow traffic to core services like Google Meet, YouTube, Chrome update servers, and Google Cloud Platform (GCP) to…
Attackers have stepped up their tactics by deploying stealthy backdoors disguised as legitimate WordPress components, ensuring persistent administrative access even…
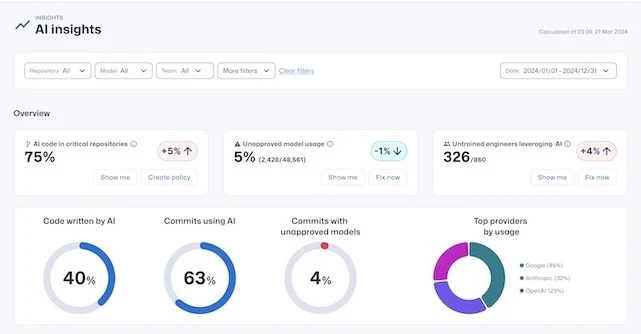
Secure Code Warrior has launched a beta program to expand the AI capabilities of its Trust Agent product. The new…