Author: Cybernoz
Sep 25, 2025Ravie LakshmananVulnerability / Network Security Cisco has warned of a high-severity security flaw in IOS Software and IOS…
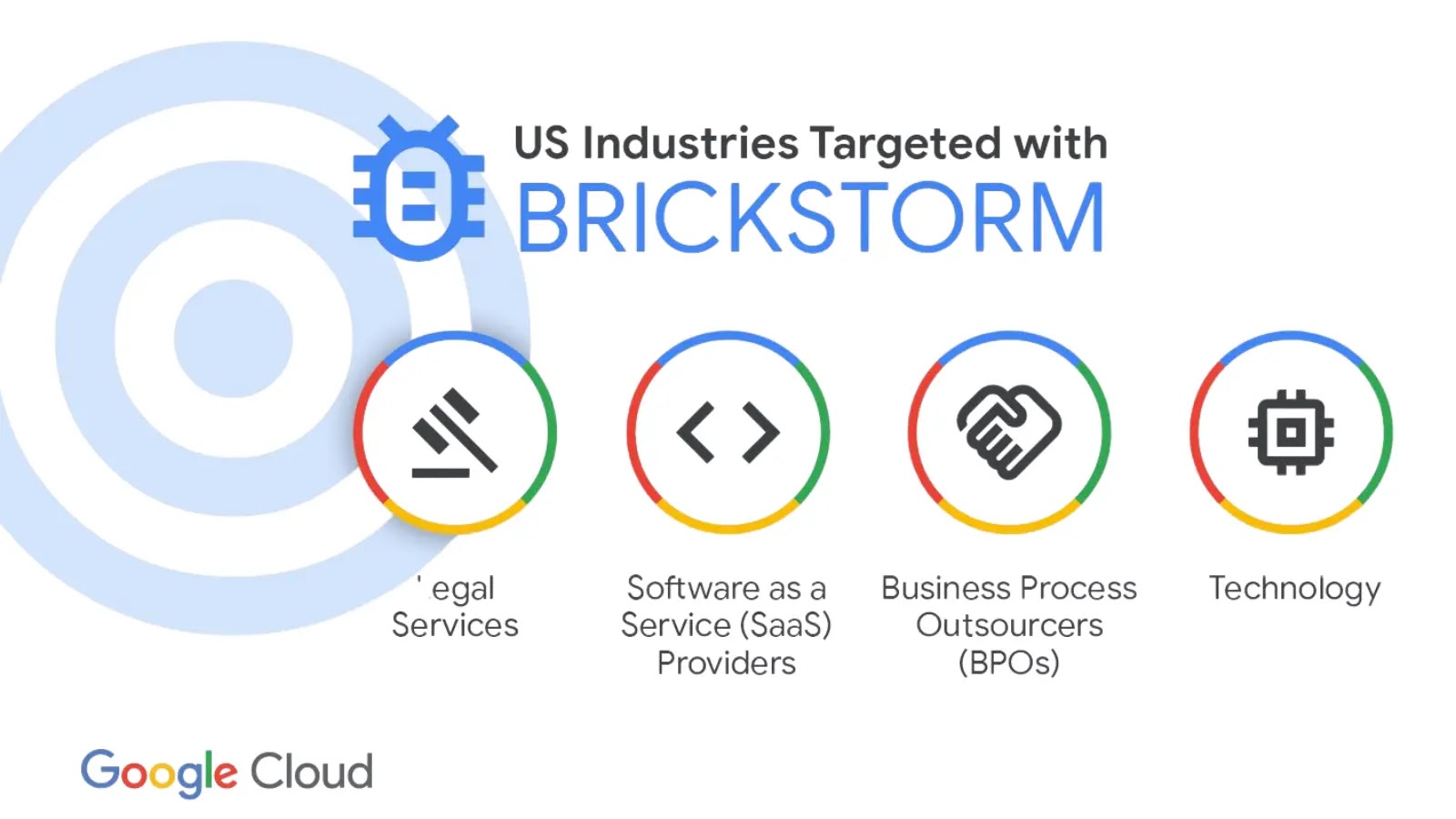
Google’s Threat Intelligence Group (GTIG) and Mandiant have published an analysis of the BRICKSTORM backdoor espionage malware, which it attributes…
A severe vulnerability in the Linux kernel’s ksmbd SMB server implementation has been disclosed, potentially allowing authenticated remote attackers to…
Security researchers have observed renewed exploit campaigns targeting an eight-year-old backdoor in Hikvision cameras to harvest configuration files, user lists,…
Luxembourg, Luxembourg, September 25th, 2025, CyberNewsWire Gcore, the global edge AI, cloud, network, and security solutions provider, today announced the…
Drones have already shown their impact in military operations, and their influence is spreading across the agricultural and industrial sectors….
A critical vulnerability in Hikvision security cameras, first disclosed in 2017, is being actively exploited by hackers to gain unauthorized…
Persistent, stealthy, and cross-platform, the BRICKSTORM backdoor has emerged as a significant threat to U.S. technology and legal organizations. Tracked…
Distributed denial-of-service (DDoS) attacks remain one of the most common and disruptive forms of cybercrime. Defenders have traditionally focused on…
Critical vulnerabilities discovered in Supermicro Baseboard Management Controller (BMC) firmware have exposed a troubling pattern where inadequate security fixes create…
A critical vulnerability in the Linux Kernel’s ksmbd file sharing component allows remote attackers to execute code with kernel privileges….
Authorities around the world have recovered $439 million from criminals following a months-long operation led by INTERPOL. The effort, called…