Author: Cybernoz
Remcos is a Remote Access Trojan (RAT) that allows attackers to gain unauthorized control over infected computers. This RAT has…
Adobe released eight security updates in September 2024, addressing 28 vulnerabilities in various products, as ColdFusion received a critical patch…
Flare, the layer-1 blockchain for data, has introduced the Flare Time Series Oracle version 2 (FTSOv2) on its mainnet. This…
Genetic testing company 23andMe will pay $30 million to settle a class action lawsuit over a 2023 data breach which…
Sep 16, 2024Ravie LakshmananFinancial Security / Malware Cybersecurity researchers are continuing to warn about North Korean threat actors’ attempts to…
The UK Foreign, Commonwealth and Development Office (FCDO) is funding efforts, led by IT security certification body Crest, to help…
In cybersecurity, a honeypot is a bait system specifically designed to attract and analyze cyber-attacks, functioning as a trap for…
Millions of D-Link routers are at risk due to several critical vulnerabilities. Security researcher Raymond identified these vulnerabilities, which have…
Boston, USA, September 16th, 2024, CyberNewsWire Analysis of millions of real-world NHI secrets by Entro Security Labs reveals widespread, significant…
Boston, USA, September 16th, 2024, CyberNewsWire Analysis of millions of real-world NHI secrets by Entro Security Labs reveals widespread, significant…
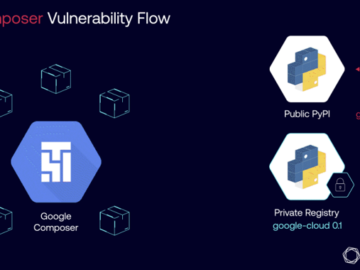
Sep 16, 2024Ravie LakshmananCloud Security / Vulnerability A now-patched critical security flaw impacting Google Cloud Platform (GCP) Composer could have…
HM Revenue & Customs’ (HMRC) publicly accessible list of non-compliant umbrella companies now features details of nearly 100 firms operating…