Author: Cybernoz
A critical vulnerability in Hikvision security cameras, first disclosed in 2017, is being actively exploited by hackers to gain unauthorized…
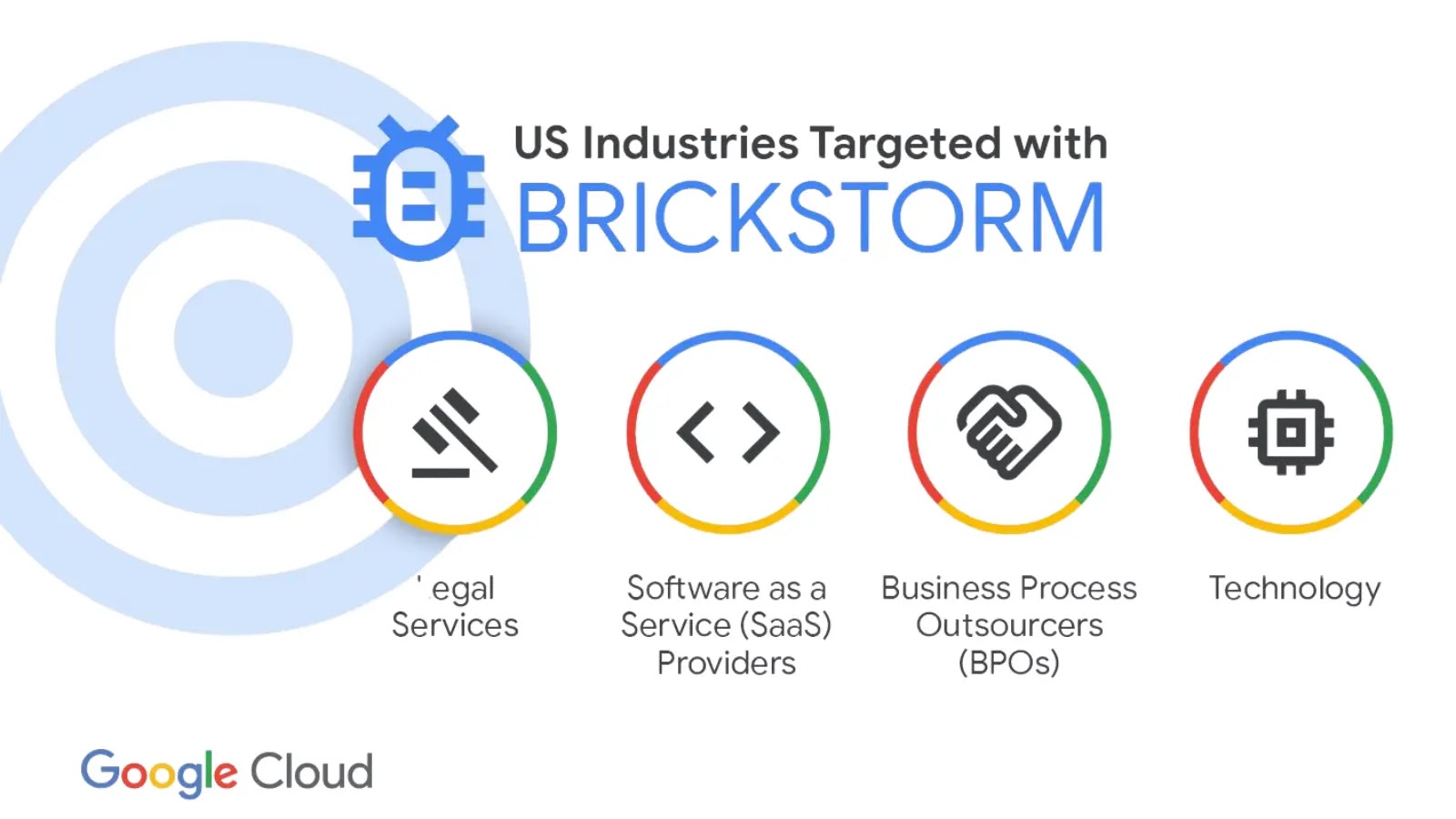
Persistent, stealthy, and cross-platform, the BRICKSTORM backdoor has emerged as a significant threat to U.S. technology and legal organizations. Tracked…
Distributed denial-of-service (DDoS) attacks remain one of the most common and disruptive forms of cybercrime. Defenders have traditionally focused on…
Critical vulnerabilities discovered in Supermicro Baseboard Management Controller (BMC) firmware have exposed a troubling pattern where inadequate security fixes create…
A critical vulnerability in the Linux Kernel’s ksmbd file sharing component allows remote attackers to execute code with kernel privileges….
Authorities around the world have recovered $439 million from criminals following a months-long operation led by INTERPOL. The effort, called…
A critical vulnerability in NVIDIA’s Merlin Transformers4Rec library allows attackers to achieve remote code execution with root privileges. Discovered by…
Managing security across dozens or even hundreds of SaaS apps has become a major headache. Each tool has its own…
A sophisticated cybercriminal campaign has emerged targeting Indonesian and Vietnamese Android users with banking trojans disguised as legitimate government identity…
A critical stored cross-site scripting vulnerability has emerged in the popular DotNetNuke (DNN) Platform, threatening websites powered by this widely-used…
Aaron Finnis, chief strategy officer at Identity and Access Management (IAM) specialist Identifly, has echoed others in the cybersecurity industry…
Australian Gas Infrastructure Group is entering the second phase of a CRM transformation, with an end goal of establishing a…