Author: Cybernoz
Despite the vulnerabilities of proximity technology, many organizations have yet to take steps to transition to more secure credentialing systems….
GitLab fixed a critical flaw in GitLab CE and GitLab EE Pierluigi Paganini September 14, 2024 GitLab addressed multiple vulnerabilities…
Sep 14, 2024Ravie LakshmananEnterprise Security / Threat Intelligence Ivanti has revealed that a newly patched security flaw in its Cloud…
Kawasaki Motors Europe (KME) has officially confirmed it was the target of a cyberattack in early September, causing temporary disruptions…
The Port of Seattle has confirmed that the Rhysida ransomware gang orchestrated the cyberattack that disrupted its systems and operations…
Image: MidjourneyPort of Seattle, the United States government agency overseeing Seattle’s seaport and airport, confirmed on Friday that the Rhysida…
Transport for London (TfL) says that all staff (roughly 30,000 employees) must attend in-person appointments to verify their identities and…
Meta is once again making headlines as it pushes forward with its generative AI plans, leveraging public content from UK…
Nuclei scans stuff for vulnerabilities. What does it scan? Modern applications, infrastructure, cloud platforms, and networks. How does it work?…
DNA testing giant 23andMe has agreed to pay $30 million to settle a lawsuit over a data breach that exposed…
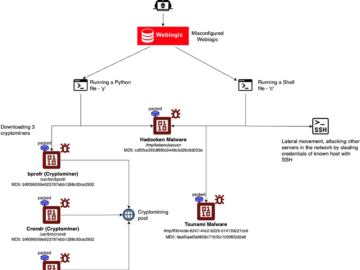
New Linux malware called Hadooken targets Oracle WebLogic servers Pierluigi Paganini September 13, 2024 A new Linux malware called Hadooken…
Hackers are targeting Oracle WebLogic servers to infect them with a new Linux malware named “Hadooken, which launches a cryptominer and…