Author: Cybernoz
The Kali Linux team has released Kali Linux 2024.3, the latest iteration of their popular penetration testing and ethical hacking…
The complexity of access has become a major challenge that is keeping CISOs up at night. Unfortunately, while the solutions…
Following the major IT outages caused by CrowdStrike, technology secretary Peter Kyle has announced the government is now classifying UK…
The inaugural iTnews Benchmark Awards: Security will celebrate the work of Australian security leaders including CISOs and CSOs for their…
In this interview, we explore Harley’s experience at DEFCON, the world’s largest hacker convention, where he took his skills to…
Tech-savvy criminals operating from luxury condos in Singapore have just learned the hard way that no corner of the globe…
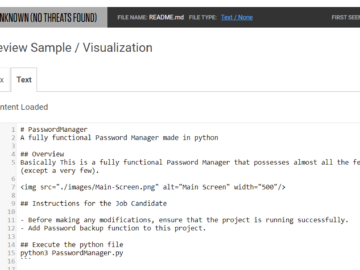
In an ongoing campaign suspected to be linked to North Korea’s Lazarus Group, malicious actors are using fake job interviews…
A Google executive told colleagues the goal for the company’s then-nascent online advertising business in 2009 was to “crush” rival…
US Federal Communications Commission chair Jessica Rosenworcel wants to see more competition to SpaceX’s internet satellite constellation Starlink. Elon Musk’s…
Learn more about bug bounty programs and how they work > The Growing Trend At HackerOne, we’ve observed a notable…
Members of the North Korean hacker group Lazarus posing as recruiters are baiting Python developers with coding test project for…
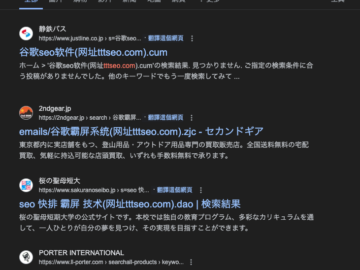
In a recent discovery, security experts have identified a suspicious new activity cluster they’re calling “DragonRank.” This activity is believed…