Author: Cybernoz
Criminal IP (criminalip.io), a distinguished leader in Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, announced that it…
Buffer overflow is a critical vulnerability in computer security that has persisted for decades. Despite technological advancements and security practices,…
When we think about cybersecurity threats we often imagine a shady hacker figure, cloaked in a black hoodie, admiring their…
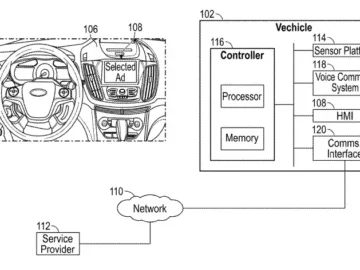
Ford has sparked privacy concerns after filing a patent for technology that would collect a wide range of driver data,…
RansomHub ransomware gang relies on Kaspersky TDSKiller tool to disable EDR Pierluigi Paganini September 11, 2024 Researchers observed the RansomHub…
Imagine a world where your inbox isn’t a monster overflowing with junk. A world where you can be confident your…
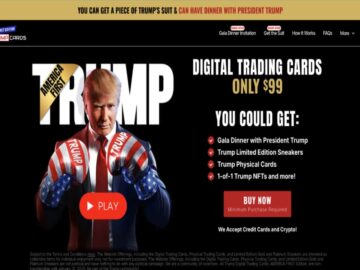
Cybercriminals target Trump’s digital trading cards using phishing sites, fake domains, and social engineering tactics to steal sensitive data. Scammers…
11 Sep Digital Transformation And Cybersecurity Strategies For SMEs Posted at 08:54h in Blogs by Di Freeze This week in…
Sep 11, 2024Ravie LakshmananCyber Crime / Hacking The Singapore Police Force (SPF) has announced the arrest of five Chinese nationals…
A day after the Indian government unveiled a series of initiatives to combat cybercrime, cybersecurity experts and activists have welcomed…
EVs face significant cyber risks due to their reliance on interconnected systems and the increasing number of public charging stations,…
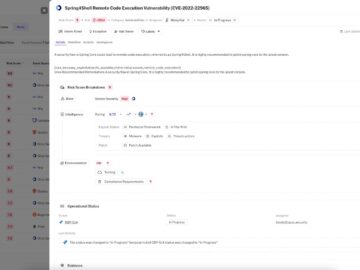
Opus’ innovative engine integrates AI-driven intelligence, contextual data and automated decision-making to drive precise, efficient vulnerability remediation. Opus Security, the…