Author: Cybernoz
Imagine a world where you never have to remember another password. Seems like a dream come true for both end…
Artificial intelligence (AI) processing rests on the use of vectorised data. In other words, AI turns real-world information into data…
Hackers have increasingly focused on web browsers, exploiting their ability to store user credentials. This shift in focus has significant…
Siemens ProductCERT has disclosed a critical vulnerability in its Industrial Edge Management systems. The vulnerability, identified as CVE-2024-45032, poses a…
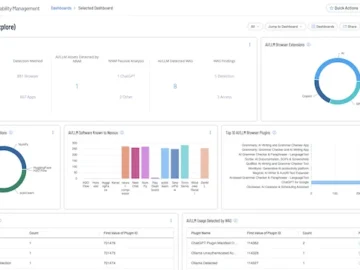
Opus Security launched its Advanced Multi-Layered Prioritization Engine, designed to revolutionize how organizations manage, prioritize and remediate security vulnerabilities. Leveraging…
Microsoft has issued four remote code vulnerabilities fixes in the September 2024 Patch Tuesday update, which it has marked as…
Developers are increasingly being targeted by sophisticated cybercriminals posing as recruiters. These attackers use fake coding tests to deliver malware,…
Adobe has issued a crucial security update for its Acrobat and Reader software on Windows and macOS platforms. This update,…
Tenable released AI Aware, advanced detection capabilities designed to surface artificial intelligence solutions, vulnerabilities and weaknesses available in Tenable Vulnerability…
Sep 11, 2024Ravie LakshmananMalware / Software Development Cybersecurity researchers have uncovered a new set of malicious Python packages that target…
In a case involving cyberstalking and obstruction of justice, John B. Hart, a 54-year-old resident of Louisville, Colorado, was sentenced…
Ivanti fixed a maximum severity flaw in its Endpoint Management software (EPM) Pierluigi Paganini September 11, 2024 Ivanti fixed a…