Author: Cybernoz
In response to the massive cyberattack that struck Columbus City in July 2024, the Columbus City Council is intensifying its…
For over a decade, the iTnews Benchmark Awards have provided a platform for organisations to gain recognition for their ambition,…
Microsoft Patch Tuesday security updates for September 2024 addressed four actively exploited zero-days Pierluigi Paganini September 11, 2024 Microsoft Patch…
Daniel Allen | 11 September 2024 at 06:53 UTC Performance is a critical factor in the usability and efficiency of…
Wix.com has announced it will stop providing services to Russian users on September 12, 2024, with all accounts from Russia,…
Small to medium-sized businesses (SMBs) are disproportionately targeted as cyber threats grow. According to the recent Hiscox annual cyber…
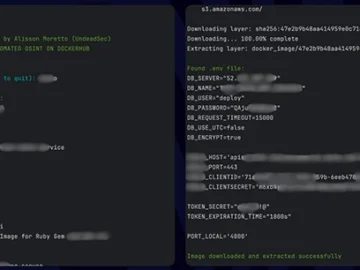
DockerSpy scans Docker Hub for images and retrieves sensitive information, including authentication secrets, private keys, and other confidential data. “DockerSpy…
Today is Microsoft’s September 2024 Patch Tuesday, which includes security updates for 79 flaws, including four actively exploited and one…
Palo Alto, USA/California, September 11th, 2024, CyberNewsWire Opus’ innovative engine integrates AI-driven intelligence, contextual data and automated decision-making to drive…
Palo Alto, USA/California, September 11th, 2024, CyberNewsWire Opus’ innovative engine integrates AI-driven intelligence, contextual data and automated decision-making to drive…
ACISO HTX | Singapore | Hybrid – View job details As an ACISO, you will formulate Agency ICT security strategy…
Microsoft has released the mandatory Windows 11 23H2 KB5043076 cumulative update to fix security vulnerabilities and make 19 improvements. KB5043076…