Author: Cybernoz
The Quad7 botnet (aka 7777 botnet, xlogin botnet) has gained attention for its use of compromised TP-Link routers to conduct…
The Zengo X Research Team has uncovered a critical flaw in WhatsApp’s “View Once” feature, designed to enhance user privacy…
Singapore, SG, September 10th, 2024, CyberNewsWire Groundbreaking technology integrates Post-Quantum Cryptography and SSL security for the next generation of Face-based…
Singapore, SG, September 10th, 2024, CyberNewsWire Groundbreaking technology integrates Post-Quantum Cryptography and SSL security for the next generation of Face-based…
Users of Zyxel network-attached storage (NAS) devices are urged to implement hotfixes addressing a critical and easily exploited command injection…
Kenya has issued a strong call to East African governments to enhance investment in cybersecurity as a critical measure to…
U.S. CISA adds SonicWall SonicOS, ImageMagick and Linux Kernel bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September 10, 2024…
Zyxel has issued critical hotfixes to address a command injection vulnerability identified in two of its Network Attached Storage (NAS)…
Charles Darwin School in Biggin Hill, London, has been forced to close its doors following a sophisticated ransomware attack temporarily….
Ransomware attacks typically cause significant disruptions for both public and private sector organizations, often halting operations for days. In a…
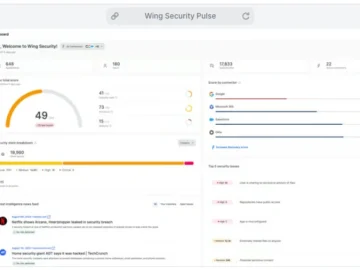
Wing Security has released SaaS Pulse, a free tool for SaaS security management, offering organizations actionable insights and continuous oversight…
As the 2024 United States presidential election is scheduled for November 5, the country is gearing up for what could…