Author: Cybernoz
As technology becomes more integral to our daily lives and business operations, cyber threats are growing increasingly, often outpacing traditional…
Elastic has disclosed two critical vulnerabilities affecting Kibana, the popular data visualization and exploration tool used with Elasticsearch. These vulnerabilities,…
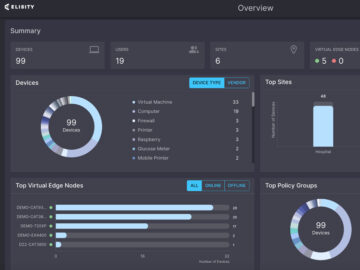
I was thrilled to catch up with Elisity during Black Hat USA 2024. Elisity’s platform makes it easy for IT,…
But X also makes it clear the onus is on the user to judge the AI’s accuracy. “This is an…
Every new technology trend opens up new attack vectors for cybercriminals. With an ongoing cybersecurity skills shortage, the need for…
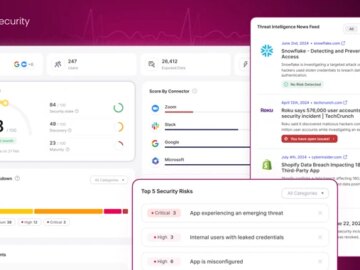
Sep 09, 2024The Hacker NewsSaaS Security / Risk Management Designed to be more than a one-time assessment— Wing Security’s SaaS…
Suncorp has built a generative AI engine it is calling ‘SunGPT’ to improve insurance agents’ access to information. Suncorp’s Kranthi…
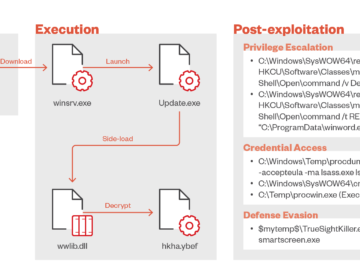
TIDRONE APT targets drone manufacturers in Taiwan Pierluigi Paganini September 09, 2024 A previously undocumented threat actor tracked TIDRONE targets…
The Fog, a ransomware variant belonging to the STOP/DJVU family that was formerly targeting educational and recreational SECTORS, has turned…
Multi-Factor Authentication (MFA) has long been heralded as a cornerstone of secure digital practices. However, the traditional forms of MFA,…
Cyberattacks and data breaches are running rampant in enterprises, causing havoc and interrupting business operations. These nuisances are the last…
LinkedIn Used by Scammers to Distribute Malware: A New Threat LinkedIn, a leading platform for professional networking, is now being…