Author: Cybernoz
While software-defined wide area networks (SD-WANs) evolved from the need to provide branch offices with access to corporate applications and…
U.S.-based car rental company Avis has reported a cyberattack, revealing that threat actors have exfiltrated data from its systems. Customers…
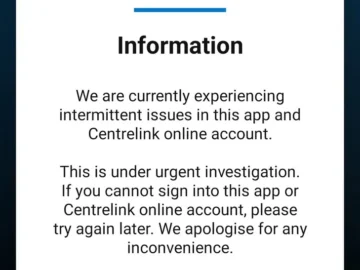
A massive disruption recently impacted Centrelink’s app and website, leaving many Australians unable to access crucial social security services. As…
The US Department of Justice plans to issue an outline by December on what Google must do to restore competition…
Multiple malware families delivered exploiting GeoServer GeoTools flaw CVE-2024-36401 Pierluigi Paganini September 09, 2024 Multiple threat actors actively exploited the…
Progress Software has issued an emergency fix for a maximum (10/10) severity vulnerability impacting its LoadMaster and LoadMaster Multi-Tenant (MT)…
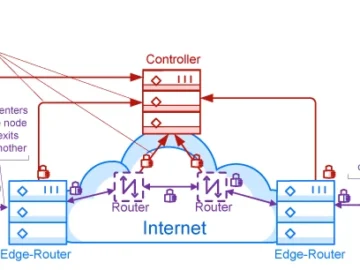
OpenZiti is a free, open-source project that embeds zero-trust networking principles directly into applications. Example of an OpenZiti overlay network…
Highline Public Schools, a district serving 17,500 students just south of Seattle, was forced to cancel classes on Monday due…
Telegram boss Pavel Durov said on Friday that the messaging app would tackle criticism of its content moderation and remove…
A new Group-IB report highlights an ongoing campaign by the North Korean Lazarus Group, known as the “Eager Crypto Beavers”…
Cybercriminals are beginning to take advantage of the new malicious options that large language models (LLMs) offer them. LLMs make…
The U.S. government and a coalition of international partners have officially attributed a Russian hacking group tracked as Cadet Blizzard…