Author: Cybernoz
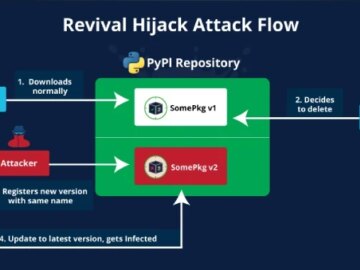
Sep 04, 2024Ravie Lakshmanan A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited…
The £1.15bn put aside to cover the costs of the Post Office Horizon scandal won’t go near meeting the bill,…
Sami Khoury, a veteran cybersecurity leader and the head of the Canadian Centre for Cyber Security (CCCS), has announced his…
Access control is fundamental to operating system (OS) security. It ensures that only authorized processes can perform specific actions on…
“North Korean malicious cyber actors conducted research on a variety of targets connected to cryptocurrency exchange-traded funds (ETFs) over the…
Sep 04, 2024Ravie LakshmananVulnerability / Network Security Zyxel has released software updates to address a critical security flaw impacting certain…
Anglian Water is the largest water and wastewater company in England and Wales. In its Water resources management plan for…
The Securities and Exchange Commission (SEC) announced that it has reached a settlement with Galois Capital Management LLC, a Florida-based…
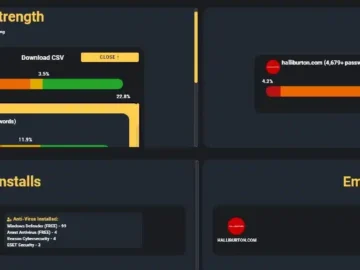
US Oilfield services giant Halliburton has confirmed that a cyberattack in August led to unauthorized third-party access and the removal…
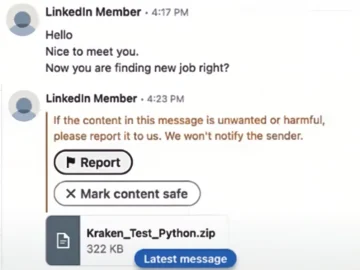
Sophisticated threat actors, like those behind the ViperSoftX malware from 2020, often make use of existing tools to save time…
In today’s digital landscape, Advanced Persistent Threats (APTs) pose a significant challenge to organizations across various sectors. Unlike standard cyberattacks…
Information security is essentially an information risk management discipline. By rendering many information systems inoperable, the global outage precipitated by…