Author: Cybernoz
Revolutionizing Cybersecurity with Automated Security Validation In a conversation with Jay Mar-Tang, Field CISO at Pentera, it became clear that…
Remote work offers benefits like reduced costs and wider recruitment but also increases cybersecurity risks. To protect your business, provide…
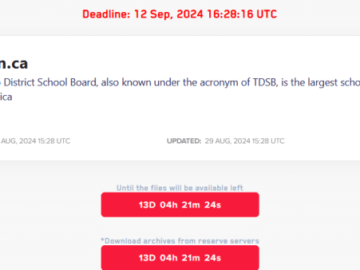
On the same day as LockBit ransomware gang claimed attack on the largest district school board in Canada, the Board…
The Federal Trade Commission (FTC) proposes a $2.95 million penalty on security camera vendor Verkada for multiple security failures that enabled…
DeadXInject, the group behind AresLoader and AiDLocker ransomware, is offering a new Malware-as-a-Service (MaaS) called ManticoraLoader. Advertised on underground forums…
Google, the prominent American technology conglomerate, has recently issued a significant warning to users of Safari and Chrome browsers. This…
Threat actors linked to the RansomHub ransomware group encrypted and exfiltrated data from at least 210 victims since its inception…
Hackers abuse Google Sheets to covertly store and transmit stolen data or execute malicious scripts, taking advantage of its trusted…
Scammers are using domain spoofing, phishing and other tactics to steal customer information from pizza restaurants, especially in Canada. Discover…
Lockbit gang claims the attack on the Toronto District School Board (TDSB) Pierluigi Paganini September 02, 2024 The Toronto District…
The hacktivist group Head Mare has leveraged a vulnerability in WinRAR to infiltrate and encrypt systems running on Windows and…
The Internet of Things (IoT) is a boom which has come with the ongoing industrial progress and revolution offering something…