Author: Cybernoz
Aug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers…
31 Aug ‘Time-Travelling’ Software Could Bankrupt Hackers Posted at 09:46h in Blogs by Di Freeze This week in cybersecurity from…
Recent studies have estimated that as many as 90% of successful cyberattacks and 70% of data breaches originate at the endpoint….
The Voldemort Malware campaign is spreading globally with over 20,000 phishing emails to more than 70 organizations, with a peak…
Pavel Durov, the founder and CEO of the communication app Telegram, was arrested in France on Saturday as part of…
The city of Columbus has obtained a temporary restraining order against cybersecurity expert David L. Ross Jr., also known as…
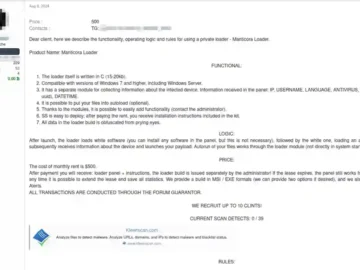
ManticoraLoader, a new malware-as-a-service (MaaS), was observed on the cybercriminal XSS forum being distributed by ‘DarkBLUP,’ an alias that was…
From refusing to cooperate with spyware abuse investigations to cracking down on its blatant misuse, Poland has come a full…
In a recent attack, a North Korean threat actor leveraged a zero-day vulnerability in Google’s Chromium browser to deploy the…
Fortra fixed two severe issues in FileCatalyst Workflow, including a critical flaw Pierluigi Paganini August 30, 2024 Cybersecurity and automation…
Windows 11’s Spotlight feature is a pretty nice way to jazz up your desktop background with different wallpapers and fun…
Security researchers have found a vulnerability in a key air transport security system that allowed unauthorized individuals to potentially bypass…