Author: Cybernoz
Nvidia has posted a 154% increase in revenue for its datacentre business in the second quarter of 2025, compared with…
Since surfacing in February 2024, RansomHub ransomware affiliates have breached over 200 victims from a wide range of critical U.S….
Google’s Threat Analysis Group (TAG) has reported the discovery of multiple exploit campaigns targeting Mongolian government websites, spanning from November…
The latest edition of Suse’s Securing the cloud report has found that almost every IT decision-maker polled is concerned about…
At Black Hat 2024, I had the opportunity to speak with Jasson Casey, CEO of Beyond Identity, about their groundbreaking…
Another innovative industry leader I had the pleasure of speaking with was Michael Bargury, Co-Founder and CTO of Zenity, a…
Job automation is 40% more likely to affect women than men, according to research by Code First Girls and Tech…
Microsoft has released the August 2024 preview update for Windows 10, version 22H2, with fixes for issues causing system freezes…
Researchers from Mandiant and Google have uncovered how cybercriminals are repurposing digital analytics and advertising tools to enhance their malicious…
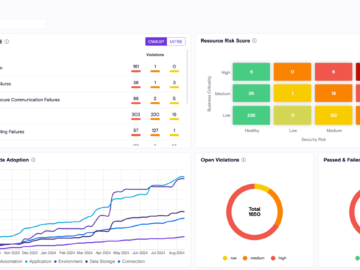
As cloud environments continue to expand, so do the threats targeting them. In today’s fast-paced digital world, attacks on cloud…
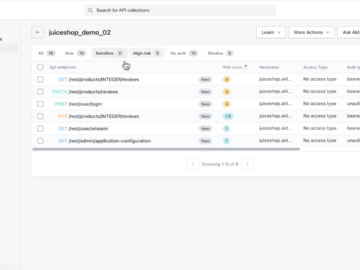
As APIs become the backbone of digital transformation, they also represent one of the biggest security risks to organizations. According…
Aug 29, 2024Ravie LakshmananBrowser Security / Vulnerability Cybersecurity researchers have flagged multiple in-the-wild exploit campaigns that leveraged now-patched flaws in…