Author: Cybernoz
While there is no shortage of hype surrounding artificial intelligence (AI), businesses are beginning to realise just how difficult it…
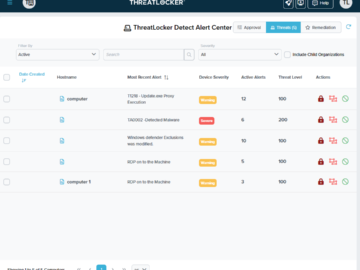
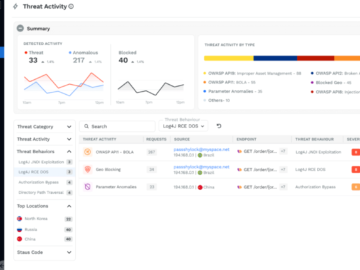
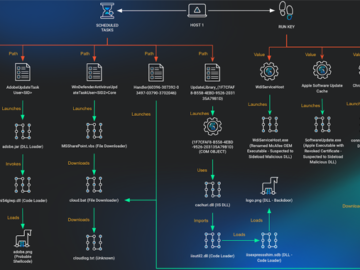
In the rapidly evolving world of cybersecurity, incidents frequently arise when malicious code finds its way into trusted environments. These…
Attending Black Hat 2024 with Cyber Defense Magazine is always an enlightening experience, giving me the opportunity to interview several…
Aug 29, 2024Ravie LakshmananCyber Espionage / Malware A non-profit supporting Vietnamese human rights has been the target of a multi-year…
Nominations are open for the 2024 Security Serious Unsung Heroes cyber security awards, recognising the exceptional talent in the UK…
Image: Midjourney The Corona Mirai-based malware botnet is spreading through a 5-year-old remote code execution (RCE) zero-day in AVTECH IP…
A malicious AutoIT-compiled executable has been discovered that attempts to open Gmail login pages using popular browsers and possesses capabilities…
A sophisticated VPN phishing and vishing campaign targeting over 130 US organizations uses social engineering tactics like phone calls and…
Check Point Software Technologies has officially announced its intention to acquire Cyberint, a pioneer in External Risk Management solutions; although…
Pavel Durov, the founder and chief executive of Telegram, has been placed under formal investigation by a French judge over…
Ransomware-as-a-Service (RaaS) significantly lowers the technical barriers for threat actors to launch ransomware attacks, even it also enables threat actors…
In recent years, elite commercial spyware vendors like Intellexa and NSO Group have developed an array of powerful hacking tools…