Author: Cybernoz
Aug 29, 2024Ravie LakshmananOnline Crime / Privacy French prosecutors on Wednesday formally charged CEO Pavel Durov with facilitating a litany…
The NIS2 Directive is one of the most recent efforts of the EU legislator to boost cybersecurity across the bloc…
In the aftermath of the CrowdStrike IT outage, new research has uncovered a critical vulnerability within financial institutions regarding supply…
The threat of deepfakes lies not in the technology itself, but in people’s natural tendency to trust what they see….
The Wireshark Foundation has announced the release of Wireshark 4.4.0, bringing a host of new features, improvements, and bug fixes…
However much of the technology in use today can still faithfully serve its purpose long after its warranty is expired….
BlackByte ransomware group is leveraging a newly discovered VMware ESXi vulnerability and VPN access to launch a new wave of…
CrowdStrike (CRWD) reported better than expected sales and earnings for the quarter that ended July 31 late today, but the…
DICK’S Sporting Goods, the largest chain of sporting goods retail stores in the United States, disclosed that confidential information was…
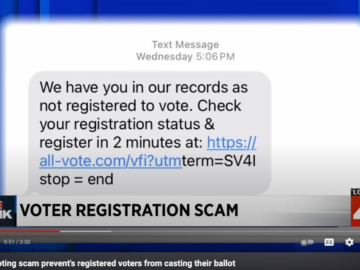
Multiple media reports this week warned Americans to be on guard against a new phishing scam that arrives in a…
The South Korea-aligned cyberespionage group APT-C-60 has been leveraging a zero-day code execution vulnerability in the Windows version of WPS…
The race to adopt AI-driven solutions has opened up new opportunities for businesses but has also introduced unprecedented risks in…