Author: Cybernoz
A severe Stored Cross-Site Scripting (XSS) vulnerability in the Prompt module of the DNN Platform enables low-privilege attackers to inject…
A cross-border cryptocurrency scam has left investors across Europe with losses of more than €100 million. Authorities in several countries…
The U.S. Secret Service said it has dismantled a massive telecommunications threat in the New York tri-state area that could…
In the light of recent supply chain attacks targeting the NPM ecosystem, GitHub will implement tighter authentication and publishing rules…
A sophisticated cybercrime campaign has emerged that transforms legitimate AWS infrastructure into weaponized attack platforms through an innovative combination of…
Kali Linux 2025.3 has arrived, bringing a wave of improvements, updated firmware support, and a suite of ten new security…
The Federal Bureau of Investigation (FBI) has issued a critical Public Service Announcement (PSA) revealing that cybercriminals are creating fake,…
Web performance and security company Cloudflare reported on Tuesday that its systems blocked another record-breaking distributed denial-of-service (DDoS) attack. The…
A sophisticated new malware family dubbed YiBackdoor has emerged in the cybersecurity landscape, posing a significant threat to organizations worldwide….
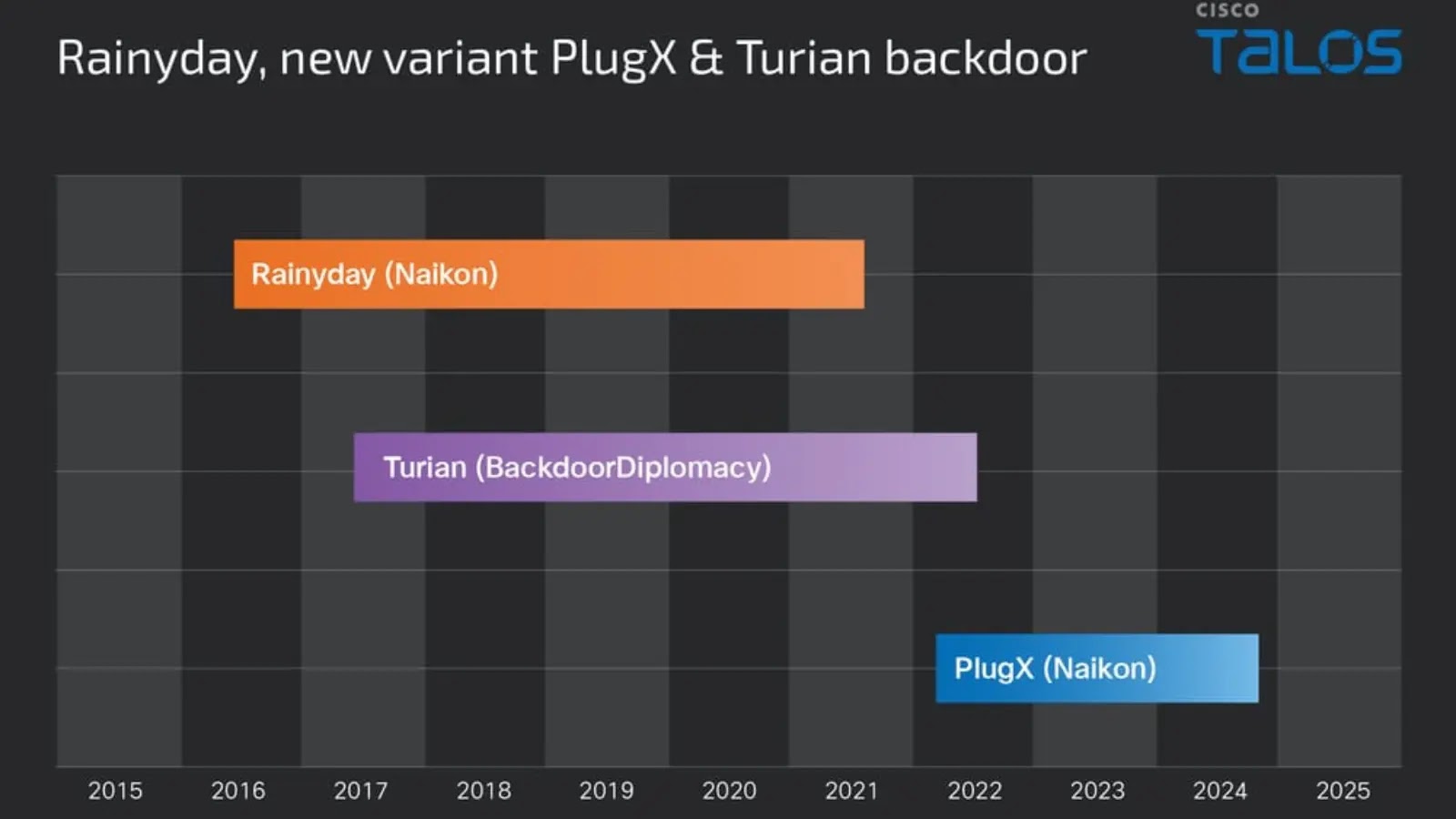
Cisco Talos has uncovered a sophisticated, long-running campaign active since 2022 that leverages DLL search order hijacking to deliver a…
OffSec has released Kali Linux 2025.3, the most up-to-date version of its popular penetration testing and digital forensics platform. What’s…
By Mandar Patil, Founding Member and SVP – Global Sales and Customer Success, Cyble At 02:17 a.m., the SOC phone…