Author: Cybernoz
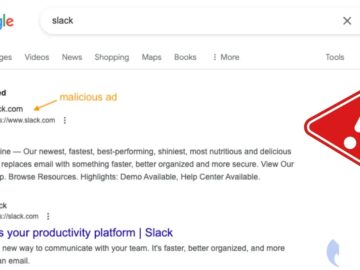
Cybercriminals have been exploiting Google search ads to deliver malicious payloads through seemingly legitimate ads for the popular communication tool…
I was thrilled to catch up with Checkmarx during Black Hat USA 2024. Cloud development transformation has ushered in a…
In recent discussions, we’ve explored how ransomware attacks are carried out, their common targets, and the impact on affected companies….
After peaking in late 2023, the ransomware industry is beginning to stabilize in productivity, with notable developments in ransomware targets,…
Aug 23, 2024Ravie LakshmananEndpoint Security / Data Privacy Cybersecurity researchers have uncovered a new information stealer that’s designed to target…
To date, most technology solutions focused on vulnerability management have focused on the prioritization of risks. That usually took the…
INE Security, a global cybersecurity training and certification provider, recently launched initiatives with several higher education institutions in an ongoing…
In the first six months of 2024, Hiya flagged nearly 20 billion calls as suspected spam – more than 107…
A sophisticated China-linked cyber espionage group, known as Velvet Ant, has been discovered exploiting a zero-day vulnerability in Cisco NX-OS…
Despite the increasing number of cybersecurity tools available, attacks continue to succeed at an alarming rate. Studies show that more…
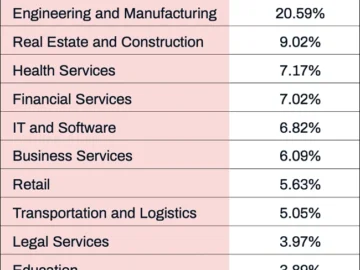
Vulnerability management has become more critical than ever as the global cost of cybercrime is projected to reach $10.5 trillion…
As security and identity management become increasingly more complex with 60% of breaches attributed to insider threats, compromising on access…