Author: Cybernoz
Senior executives are prime targets for cybercriminals, with 72% of surveyed cybersecurity professionals in the US reporting that cyberattacks have…
Things change fast in the world of data privacy. Just earlier this year, the question I was being asked most…
Aug 22, 2024Ravie LakshmananDatabase Security / Cryptocurrency Cybersecurity researchers have unpacked a new malware strain dubbed PG_MEM that’s designed to…
A security researcher discovered a bug in iOS on Wednesday that can cause iPhones and iPads to briefly crash when…
There’s been an alarming increase in ransomware attacks over the past year, alongside significant shifts in the tactics and strategies…
95% of cybersecurity experts express low confidence in GenAI security measures while red team data shows anyone can easily hack…
Halliburton, a leading oilfield services company, is currently grappling with a significant cyberattack that has disrupted operations at its Houston…
Google has recently addressed a high-severity zero-day vulnerability in its Chrome browser, identified as CVE-2024-7971. This vulnerability involves a type…
Bank of Queensland Group has directly linked plans to cut “up to 400 full-time equivalent roles” to its ongoing digital…
Medibank is expecting to have completed “the vast majority” of its cyber security uplift following a 2022 data breach by…
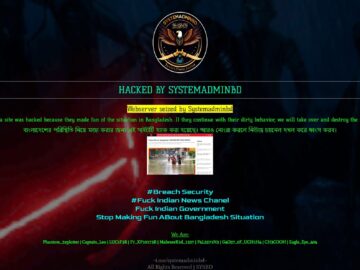
Bangladeshi hackers “SYSTEMADMINBD” defaced Zee Media’s website, accusing them of mocking the situation in Bangladesh amid severe flooding. The hack…
Today, Google released a new Chrome emergency security update to patch a zero-day vulnerability tagged as exploited attacks. “Google is…