Author: Cybernoz
Previously unseen Msupedge backdoor targeted a university in Taiwan Pierluigi Paganini August 20, 2024 Experts spotted a previously undetected backdoor,…
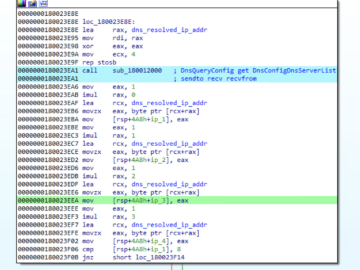
Unknown attackers have deployed a newly discovered backdoor dubbed Msupedge on a university’s Windows systems in Taiwan, likely by exploiting…
On the 8th of October in 2027, an alien craft was seen entering the atmosphere over the Atlantic around 600…
According to user reports following this month’s Patch Tuesday, the August 2024 Windows updates are breaking dual boot on Linux…
A severe security flaw has been discovered in GiveWP, a popular WordPress donation plugin with over 100,000 active installations. The…
I was thrilled to catch up with ForAllSecure during Black Hat USA 2024. ForAllSecure is an organization of hackers, developers,…
Meet TodoSwift, a malicious application that masquerades as a PDF downloader. Crafted by the BlueNoroff threat group, TodoSwift leverages Apple’s Swift/SwiftUI…
The case against SolarWinds was filed by the Securities and Exchange Commission (SEC), a government agency that has interpreted its…
In modern business, cybersecurity is not merely a technical concern but a crucial financial safeguard. With cyber threats growing in…
Since August 14, 2024, the Federal Office for Information Security (BSI) in Germany has begun issuing security labels for IT…
A hacker compromised Unicoin’s Google Workspace (formerly G-Suite) account and changed the passwords for all company employees, locking them out…
BlindEagle (APT-C-36) is a Latin American Advanced Persistent Threat group that has been active since 2018. It targets the governmental,…