Author: Cybernoz
CISA has added a critical Jenkins vulnerability that can be exploited to gain remote code execution to its catalog of…
Recently cybersecurity researchers at Check Point discovered a new malware dubbed “Styx Stealer,” capable of stealing browser and instant messenger…
AI SPERA, a leading Cyber Threat Intelligence (CTI) company, has announced a strategic partnership with Hackers Central, a major cybersecurity…
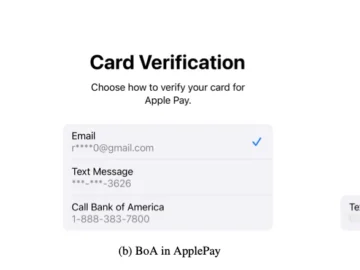
Fraudsters can add stolen payment cards to digital wallet apps and continue making online purchases even after victims’ report the…
Compute Express Link (CXL), the technology for connecting memory, was among the themes at last week’s Future of Memory and Storage…
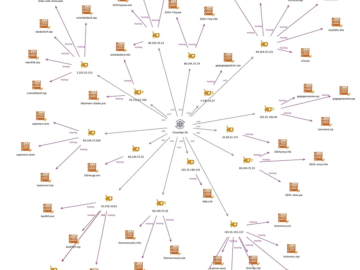
Researchers uncovered new infrastructure linked to the cybercrime group FIN7 Pierluigi Paganini August 19, 2024 Team Cymru, Silent Push and…
Toyota’s U.S. branch has reportedly suffered a massive data breach, resulting in the unauthorized release of approximately 240 GB of…
The recent electoral success of the Labour Party opens up the possibility of significant changes in the nation’s cyber security…
Cisco Talos has identified eight security vulnerabilities in Microsoft applications running on the macOS operating system, raising concerns about potential…
The US National Institute of Standards and Technology (NIST) has announced three standards for post-quantum cryptography (PQC). But for PQC…
Suspected hackers behind the heist of $14,000,000 worth of cryptocurrency from blockchain tech firm Holograph was arrested in Italy after…
A critical vulnerability tracked as CVE-2024-7646, has been uncovered in the widely used ingress-nginx Kubernetes controller. The flaw allows attackers…