Author: Cybernoz
The Tor Project has announced the release of Tor Browser 13.5.2, which includes significant security updates and improvements, mainly focusing…
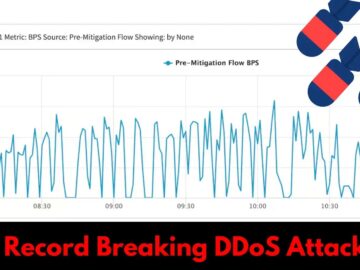
A record-breaking Distributed Denial of Service (DDoS) attack unleashed 419 terabytes of malicious traffic over 24 hours. This unprecedented event,…
A researcher has developed a downgrade attack that can make Windows machines covertly, persistently and irreversibly vulnerable, even if they…
The United States has intensified its efforts to combat cyber threats by offering a substantial reward for information leading to…
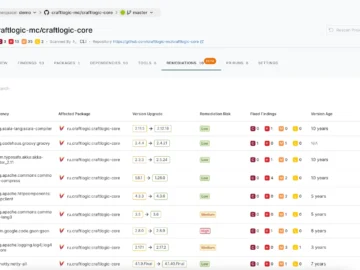
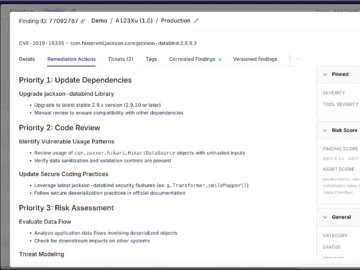
Endor Labs unveiled two capabilities, Upgrade Impact Analysis and Endor Magic Patches, that fix an expensive and time-consuming problem in…
A significant security flaw in Microsoft Entra ID identity and access management service has been exposed, revealing that privileged users…
FBI and CISA update a joint advisory on the BlackSuit Ransomware group Pierluigi Paganini August 08, 2024 FBI and CISA…
London, UK & Antwerp, Belgium – Aug 06 – Intigriti, a leading platform in vulnerability management and bug bounty, announces…
A critical vulnerability in Cisco’s Smart Software Manager On-Prem (SSM On-Prem) has surfaced, allowing unauthenticated, remote attackers to change user…
ArmorCode has launched AI Remediation in its ArmorCode ASPM Platform to help resolve security issues faster, put security expertise in…
Aug 08, 2024The Hacker NewsArtificial Intelligence / Network Security The Immersive Experience Happening This September in Las Vegas! In an…
The City of North Miami has alerted the public to a possible cyber incident impacting its network systems, resulting in…