Author: Cybernoz
Singapore authorities have successfully intercepted and reclaimed over USD 40 million defrauded in a sophisticated business email compromise (BEC) scam….
Resecurity (USA), a global leader in cybersecurity and risk management solutions serving major Fortune 500 companies and government agencies, has…
Thank you for joining! Access your Pro+ Content below. 6 August 2024 Migrating to S/4Hana – how the Co-op made…
SentinelOne (NYSE: S), a prominent figure in AI-driven security, has announced the appointment of Alex Stamos as its new Chief…
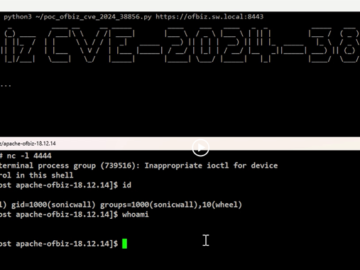
A critical zero-day vulnerability in Apache OFBiz, an open-source enterprise resource planning (ERP) system, has been discovered that could allow…
Aug 06, 2024Ravie LakshmananMobile Security / Vulnerability Google has addressed a high-severity security flaw impacting the Android kernel that it…
At HackerOne, we’ve witnessed our parents craft impressive solutions to blend their professional and personal worlds. We wanted to hear…
Implementing multicloud solutions is becoming increasingly paramount for organizations seeking to drive their business forward in the coming years. As…
Calibrated Healthcare, LLC (“Calibrated”) recently filed a notice of a data breach with the Attorney General of California following the…
In this Help Net Security interview, Bruno Kurtic, President and CEO at Bedrock Security, discusses the role of data visibility…
Aug 06, 2024Ravie LakshmananEnterprise Security / Vulnerability A new zero-day pre-authentication remote code execution vulnerability has been disclosed in the…
Let’s talk about a couple of recent horror stories. Late last year, a Chevrolet dealership deployed a chatbot powered by…