Author: Cybernoz
The Black Basta ransomware gang has shown resilience and an ability to adapt to a constantly shifting space, using new…
Global cybercrime costs are projected to soar from $9.22 trillion in 2024 to $13.82 trillion by 2028.1 In the United…
Dark Angels Ransomware Group’s $75M Jackpot: Zscaler’s ThreatLabz 2024 Ransomware Report reveals how this elite gang targets select corporations, siphoning…
The Australian government has long advised ransomware victims against paying ransoms, arguing that doing so does not guarantee receiving a…
We have previously reported on the brand impersonation issue with Google ads: users who search for popular keywords are shown…
Google Chrome has added app-bound encryption for better cookie protection on Windows systems and improved defenses against information-stealing malware attacks. As Chrome software…
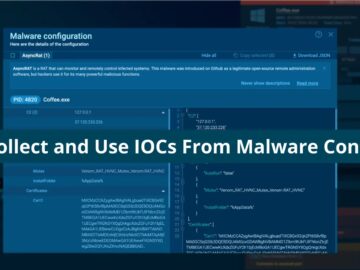
Indicators of Compromise (IOCs) are key forensic data points used to detect security breaches. They include file hashes, suspicious IP…
The appetite for food delivery apps has grown exponentially—more than 2.85 billion people used them globally last year. In the…
British Library chief executive Roly Keating has said that the organisation is aiming to have some key services that remain…
The City of Columbus, Ohio, says it’s investigating whether personal data was stolen in a ransomware attack on July 18,…
Cybercriminals have launched a smishing campaign targeting iPhone users in India, impersonating India Post. Malicious iMessages falsely claim a package…
A Google Workspace vulnerability exposed thousands of accounts after hackers bypassed email verification. Learn how to protect your Workspace account…