Author: Cybernoz
By exploiting OS command injection vulnerabilities, threat actors can run arbitrary commands on a host operating system to obtain unauthorized…
A critical local privilege escalation vulnerability has been discovered in RaspAP, an open-source project designed to transform Raspberry Pi devices…
The government is ploughing millions of pounds into five new quantum hubs in Glasgow, Edinburgh, Birmingham, Oxford and London to…
Onyx Sleet, a cyber espionage group also known as SILENT CHOLLIMA, Andariel, DarkSeoul, Stonefly, and TDrop2, mainly targets the military,…
Ukraine launches a massive cyber attack on Russia, disrupting ATM services, online banking, and financial institutions. Reportedly, a series of…
In a key step to improve maritime safety in the Asia-Pacific region, top diplomats from Japan, the United States, Australia,…
Void Banshee, a threat actor, has been exploiting a critical MSHTML vulnerability, CVE-2024-38112, to distribute the Atlantida InfoStealer malware. This…
A malicious campaign emerged on June 21, 2024, distributing a JavaScript file hosted on grupotefex.com, which executes an MSI installer,…
More organizations rely on cloud platforms to reap the benefits of scalability, flexibility, availability, and reduced costs. However, cloud environments…
Hackers continuously exploit malicious Python packages to attack developer environments and inject harmful code that enables them to steal sensitive…
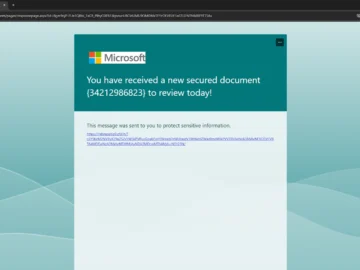
There has been an uptick in phishing campaigns leveraging Microsoft Forms this month, aiming to trick targets into sharing their…
Hackers often attack secure boot during the boot process to execute unauthorized code, which gives them the ability to bypass…