Author: Cybernoz
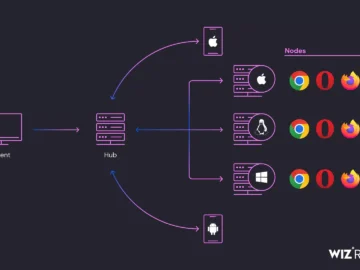
Threat actors are increasingly targeting exposed Selenium Grid services to deploy cryptominers, a campaign dubbed “SeleniumGreed.” This threat leverages the popular…
BIND updates fix four high-severity DoS bugs in the DNS software suite Pierluigi Paganini July 26, 2024 The Internet Systems…
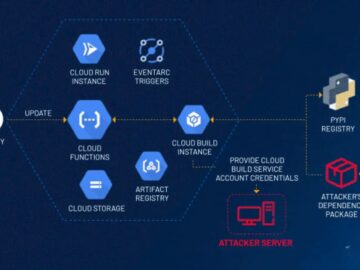
A newly discovered vulnerability in Google Cloud Platform (GCP) has raised significant security concerns among users and experts alike. The…
From €142 million to €1 billion ($1.1 billion) a year. The European Commission is pressing the accelerator on investment in…
The North Korean hacker, Rim Jong Hyok, is accused of being part of the government-backed cyberespionage group Andariel, which is…
Jul 26, 2024The Hacker NewsDigital Warfare / Cybersecurity Training “Peace is the virtue of civilization. War is its crime. Yet…
The Indian Government has once again reiterated its key strategies to strengthen its cyber defense and safeguard its citizens in…
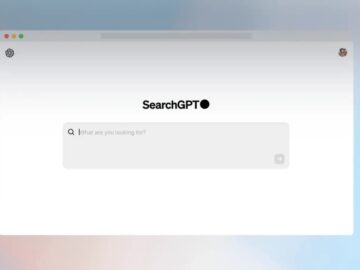
San Francisco, CA – OpenAI has announced the launch of SearchGPT, a groundbreaking prototype designed to revolutionize how users search…
The U.S. Department of Justice (DoJ) on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly…
Former government minister Vince Cable said the Post Office lied to the government to prevent the truth about the mistreatment…
Healthcare organizations are increasingly becoming prime targets for cyberattacks. The combination of limited budgets, a shortage of dedicated cybersecurity staff,…
The PKfail vulnerability is a significant security issue affecting over 200 device models of Secure Boot. PKfail is a critical…