Author: Cybernoz
American cybersecurity company KnowBe4 says a person it recently hired as a Principal Software Engineer turned out to be a…
Google has unveiled the latest version of its Chrome browser, Chrome 127, which is now available on the Stable channel….
Shared frameworks are often prone to hackers’ abuses as they have been built into various applications, which offer a range…
The Post Office always acted like the victim of “incompetent” or “criminal” subpostmasters when it faced pressure in relation to…
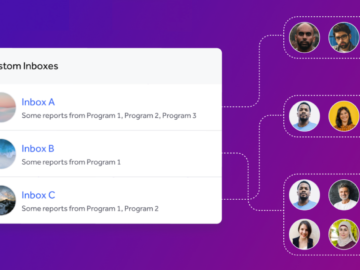
Introducing Custom Inboxes Custom Inboxes provide our enterprise customers with unparalleled flexibility in report management. Now, organizational administrators can create,…
Google Chrome now warns when downloading risky password-protected files and provides improved alerts with more information about potentially malicious downloaded files….
Malicious Python packages uploaded by “dsfsdfds” to PyPI infiltrated user systems by exfiltrating sensitive data to a Telegram bot likely…
Human-centred risk management experts Mimecast and Code42 are to come together as a single business in an acquisition that builds…
Despite having simple gameplay, the new Telegram clicker game Hamster Kombat has become very well-liked among gamers who use cryptocurrencies…
In recent years, cybersecurity threats have often involved hackers stealing identities through various digital channels to gather sensitive information. However,…
SAP has posted cloud revenue of €4.2bn, up 25% for the second quarter of 2024. The company said the increase…
Register today for mWISE™, the unique cybersecurity conference from Mandiant, now part of Google Cloud. Built by practitioners for practitioners,…