Author: Cybernoz
CrowdStrike Holdings Inc has attributed the global IT outage last week to a bug in its test software. The CrowdStrike…
Google has announced the release of Chrome 127, which is now available on the Stable channel for Windows, Mac, and…
Jul 24, 2024NewsroomSoftware Update / IT Outage Cybersecurity firm CrowdStrike on Wednesday blamed an issue in its validation system for…
Police could lawfully use bulk surveillance techniques to access messages from encrypted communications platforms such as WhatsApp and Signal following…
Cybersecurity and Infrastructure Security Agency (CISA) Director Jen Easterly acknowledged significant leadership changes within the agency. This CISA leadership change…
In a recent preliminary Post-Incident Review (PIR), cybersecurity firm CrowdStrike provided a detailed account of the events that led to…
Secure collaboration through access-sharing is a must-have feature in almost any modern application, from requesting to edit a document or…
Microsoft users across the globe should review the state of their infrastructure security setups in the wake of the botched…
Security awareness and training provider KnowBe4 recently disclosed that it inadvertently hired a fake North Korean IT worker who attempted…
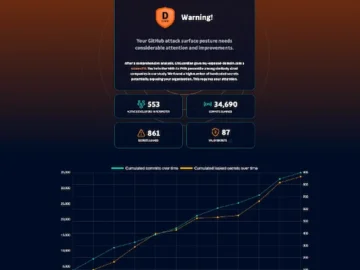
GitGuardian releases a tool to help companies discover how many secrets their developers have leaked on public GitHub, both company-related…
Microsoft has appointed Anujh Tewari as the Chief Cybersecurity Advisor for India and South Asia. Tewari announced his new role…
Jul 24, 2024NewsroomVulnerability / Software Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to…