Author: Cybernoz
CrowdStrike is warning that a fake recovery manual to repair Windows devices is installing a new information-stealing malware called Daolpu….
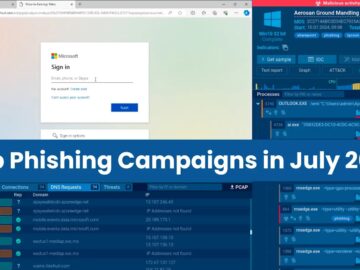
July saw a new influx of phishing and malware campaigns. The analyst team at ANY.RUN sandbox is closely monitoring all…
ClickBalance ERP provider’s cloud database exposed 769 million records, including API keys and email addresses. Learn how this cloud security…
The security operations center faces significant challenges in the form of data overload and the resulting increases in ingestion costs….
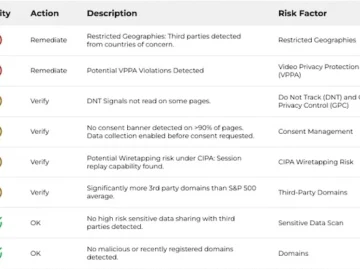
LOKKER released a new privacy solution for insurers: the ability to share on-demand web privacy risk reports with their insureds….
Jul 23, 2024NewsroomCyber Espionage / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has alerted of a spear-phishing campaign…
Hybrid multicloud storage is intended to create the best of all worlds. By mixing on-premise technology with multiple public cloud…
Stealers are one of the most used malicious tools that is used by threat actors. As such tools enable hackers…
Threat actors often attack cloud services for several illicit purposes. Google Cloud is targeted due to its extensive and powerful…
23 Jul July 2024: National Make A Difference To Children Month Posted at 09:04h in Blogs by Di Freeze This…
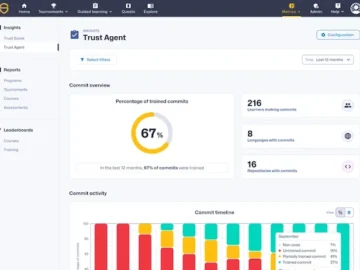
Secure Code Warrior introduced SCW Trust Agent – a solution that assesses the specific security competencies of developers for every…
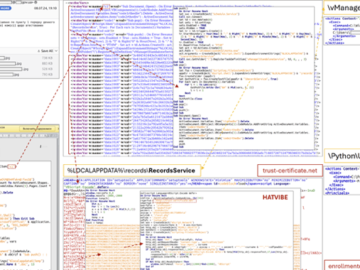
Jul 23, 2024NewsroomCyber Espionage / Chinese Hackers Organizations in Taiwan and a U.S. non-governmental organization (NGO) based in China have…