Author: Cybernoz
In recent years, the belief that macOS systems are immune to malware has been increasingly challenged. With the emergence of…
The challenge of locating and utilizing data within organizations has become increasingly problematic. Despite the abundance of data available, much…
Infamous hacker USDoD, linked to major data breaches, reveals his identity as a Brazilian citizen. Discover the implications and how…
As the field of artificial intelligence (AI) continues to evolve rapidly, aspiring professionals need a solid foundation in various topics…
Read the full article for key points from Intruder’s VP of Product, Andy Hornegold’s recent talk on exposure management. If…
The year is only halfway over, but the healthcare sector has already reported 280 cyber incidents. That’s a staggering 24%…
Cybersecurity researchers have uncovered a sophisticated phishing campaign leveraging the “Cheana Stealer” malware, which has been distributed via a VPN…
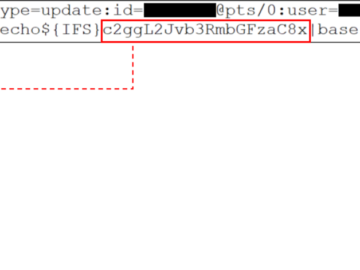
China-linked APT Velvet Ant exploited zero-day to compromise Cisco switches Pierluigi Paganini August 23, 2024 China-linked APT group Velvet Ant…
A member of a notorious Russian cybercrime group has been charged federally and appeared in U.S. District Court in Cincinnati…
I was thrilled to catch up with Horizon3.ai during Black Hat USA 2024. Most attackers don’t break in, they log…
Over time, Deep State has added more advanced features and quirks to the map. A toolbar in the bottom-left corner…
Cyber-Informed Engineering (CIE) is a new perspective on OT cyber risk – one that is being embraced by OT/engineering teams and…