Author: Cybernoz
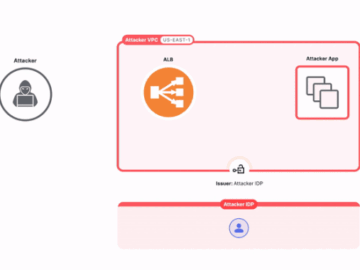
Aug 22, 2024Ravie LakshmananCloud Security / Application Security As many as 15,000 applications using Amazon Web Services’ (AWS) Application Load…
Following the sinking of his luxury yacht on Monday, Reuters has reported that the body of tech entrepreneur Mike Lynch…
SolarWinds has released a hotfix for a critical Web Help Desk vulnerability that allows attackers to log into unpatched systems…
Hackers execute several illicit activities with the help of Android malware, and they target Android due to its widespread use…
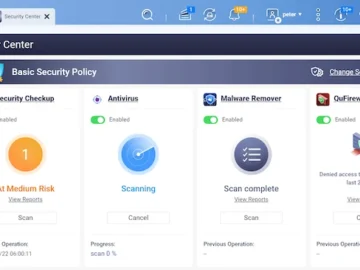
QNAP has released the QTS 5.2 NAS operating system. A standout feature of this release is the debut of Security…
I’ve been thinking a lot about the whole “data wall” thing with LLMs lately. It’s the idea that LLMs can’t…
Hackers have leaked footage and clips from several unreleased Netflix anime shows, including full episodes, online. The content was stolen…
22 Aug New Podcast Series: Steve Satterwhite On Cyber Posted at 08:58h in Blogs by Di Freeze This week in…
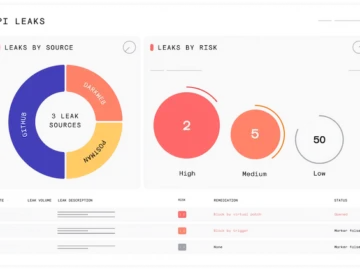
Wallarm announced its latest innovation: API Attack Surface Management (AASM). This agentless technology transforms how organizations identify, analyze, and secure…
The number of girls choosing to take computing at GCSE level is rising steadily, with 2024 seeing the third consecutive…
In response to the rise of cyberattacks targeting critical infrastructure worldwide, the Central Electricity Authority (CEA) of India has put…
The controversy surrounding Fidelity Bank Data Breach has gone a notch higher with the Nigerian bank rejections all allegations of…