Author: Cybernoz
Since October 2023, MuddyWater, which is an Iranian threat group linked to MOIS, has escalated its phishing campaigns in Middle…
18 Jul The Importance Of Women In Cybersecurity Posted at 08:54h in Blogs by Di Freeze This week in cybersecurity…
CISSP carries clout. As the world’s leading cybersecurity certification, it opens many professional opportunities worldwide. Find out what led 14…
Breaking up is hard to do, but for younger Americans today, ending a romantic relationship requires more than a heart-to-heart…
Jul 18, 2024The Hacker NewsApp Security / Security Awareness Let’s face it: AppSec and developers often feel like they’re on…
IBM has received a significant contract from the U.S. Agency for International Development (USAID) to enhance cybersecurity response efforts in…
Microsoft says the Windows 11 2023 Update has entered the broad deployment phase and is now available to all seekers…
Confidential documents from mobile forensics company Cellebrite, recently obtained and verified by 404 Media, provide a rare glimpse into the…
Cybersecurity threats continue to grow, with the threat landscape constantly evolving and hackers employing increasingly sophisticated and unpredictable methods. With…
Jul 18, 2024The Hacker NewsCybersecurity / Bot Attacks As the travel industry rebounds post-pandemic, it is increasingly targeted by automated…
The Department for Health and Social Care (DHSC) has upped its data personnel budget to £5.37m over the course of…
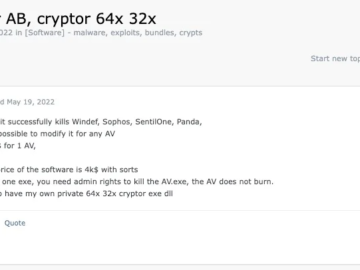
Cybercrime group FIN7 advertises new EDR bypass tool on hacking forums Pierluigi Paganini July 18, 2024 The cybercrime group FIN7…