Author: Cybernoz
If you work in the security industry, you have likely heard about the polyfill.io incident that came into the public…
Jul 17, 2024NewsroomCyber Espionage / Cryptocurrency Cybersecurity researchers have discovered an updated variant of a known stealer malware that attackers…
Women are well represented in tech leadership positions across Europe, according to half of the people asked during the annual…
A threat actor has leaked a database containing the personal information of 442,519 Life360 customers collected by abusing a flaw…
The Volcano Demon group has been discovered spreading a new ransomware called LukaLocker, which targets Idealease Inc., a truck leasing…
On May 31, 2024, as a result of the hacking 4502.9 BTC (worth approximately $308M) were stolen from the Japanese…
The Information Commissioner’s Office (ICO) has strongly reprimanded the London Borough of Hackney over a series of failings that led…
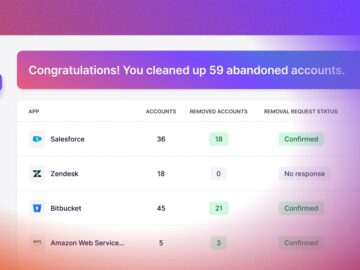
As the landscape of modern work changes, with its distributed teams and quickly evolving cloud-based technologies, maintaining access controls is…
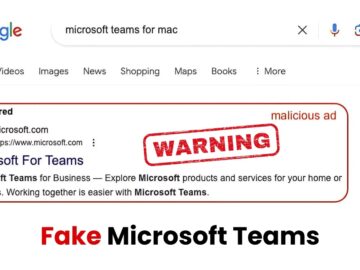
Hackers often mimic popular tools like Microsoft Teams to exploit people’s trust and familiarity with these applications. This strategy increases…
In June of this year, the Kaspersky cybersecurity firm, led by Eugene Kaspersky, was banned by the Joe Biden administration,…
Police Digital Service (PDS) CEO Ian Bell is no longer a director of the company, two weeks after it emerged…
MarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen…