Author: Cybernoz
It’s been less than 18 months since the public introduction of ChatGPT, which gained 100 million users in less than…
Jul 16, 2024NewsroomNational Security / Data Security Russian security vendor Kaspersky has said it’s exiting the U.S. market nearly a…
In this Help Net Security interview, Seth Hodgson, SVP of Engineering at Udemy, discusses effective study techniques for cybersecurity certification…
This article provides an overview of the major data breaches we covered in 2024 so far, highlighting incidents involving Trello,…
While previous Olympic games have faced cybersecurity threats, the Games of the XXXIII Olympiad, also known as Paris 2024, will…
FBI unlocked the phone of the suspect in the assassination attempt on Donald Trump Pierluigi Paganini July 16, 2024 The…
AT&T recently faced a significant cybersecurity breach involving its Snowflake account, leading to the company allegedly paying a ransom to…
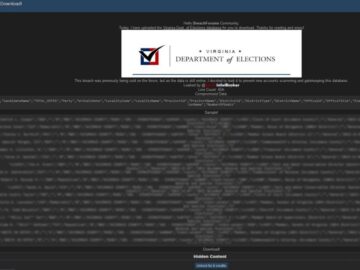
After multiple claims that Virginia election candidates’ data had been leaked surfaced in the past few weeks, the Virginia Department…
The Problems Customers Use Ethical Hackers To Solve Organizations work with ethical hackers to address a range of issues, including…
Google parent Alphabet is in advanced talks to acquire cyber security startup Wiz for roughly US$23 billion ($34 billion), a…
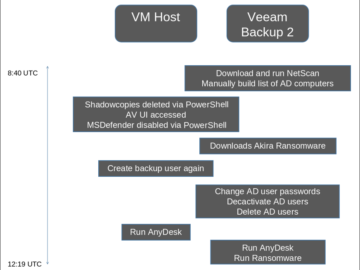
Ransomware groups target Veeam Backup & Replication bug Pierluigi Paganini July 15, 2024 Multiple ransomware groups were spotted exploiting a…
A group calling itself “NullBulge” published a 1.1-terabyte trove of data late last week that it claims is a dump…