Author: Cybernoz
Cybercrime costs trillions, rising yearly. Criminals operate globally, teaching their methods. This article explores major cyberattacks from 1962 to 2024…
Sizable fines imposed for data breaches in recent years indicate that regulators are increasingly determined to crack down on organizations…
October ransomware attack on Dallas County impacted over 200,000 people Pierluigi Paganini July 12, 2024 The ransomware attack that hit…
The face of cyber threats has transformed dramatically over the decades. At first, they emerged as hacks, viruses and denial…
Here’s a look at the most interesting products from the past week, featuring releases from AttackIQ, IT-Harvest, Pentera, Prompt Security,…
The U.S. Department of Justice (DoJ) said it seized two internet domains and searched nearly 1,000 social media accounts that…
Vyacheslav Igorevich Penchukov was sentenced to prison for his role in Zeus and IcedID operations Pierluigi Paganini July 13, 2024…
I think every creator might need to make a core decision of whether they’re doing: A PERSONAL brand on which…
Security a Top Concern During 2024 Election ‘Super-Cyle’ With an unprecedented ‘super-cycle’ of elections in 2024, almost half the world’s…
mSpy, a popular cell phone tracking software utilized by millions, has recently made headlines due to a significant cyber attack…
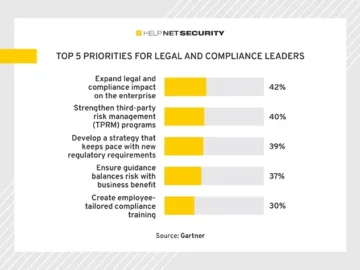
Legal, compliance and privacy leaders list strengthening their personal impact on company strategy as their top priority for 2024, according…
Jul 12, 2024NewsroomVulnerability / Software Security A critical security issue has been disclosed in the Exim mail transfer agent that…