Author: Cybernoz
AT&T, one of the largest and oldest telecoms and mobile network operators in the United States, has lost control of…
The University of Missouri, in collaboration with Amrita University, India, has released a new paper on how large language models…
IntelBroker has claimed unauthorized access to the Korean National Police Agency and is selling this access to potential buyers on…
AT&T said the company suffered a massive hacking incident as data from about 109 million customer accounts containing records of…
New AT&T data breach exposed call logs of almost all customers Pierluigi Paganini July 12, 2024 AT&T disclosed a new…
Censys warns that over 1.5 million Exim mail transfer agent (MTA) instances are unpatched against a critical vulnerability that lets…
According to recent findings by security researchers, more than 1.5 million email servers are currently vulnerable to a critical security…
Artificial intelligence is an ever-evolving subject; year by year, its landscape is expanding to different industries, and the outcome of…
The Department of Defence has engaged ServiceNow to assist with its gargantuan enterprise resource planning (ERP) system uplift, handing over…
Torrens University is looking to develop a new roadmap for its security, technology infrastructure and data operations. Torrens University, Sydney…
Germany has closed a deal with telecom providers to exclude Chinese companies such as Huawei or ZTE from the nation’s…
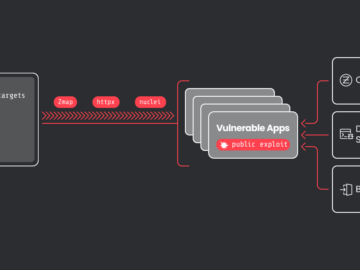
CrystalRay operations have scaled 10x to over 1,500 victims Pierluigi Paganini July 11, 2024 A threat actor known as CrystalRay…